How to Deny Write Access to Removable Drives not Protected by BitLocker in Windows 10
By default in Windows 10 every user can write files and folders to all removable storage devices they connect to the computer. The user can also delete or modify any file stored on a removable drive. Windows 10 includes an option to disable write access to all removable disks not protected by BitLocker for all users.
Advertisеment
BitLocker was first introduced in Windows Vista and still exists in Windows 10. It was implemented exclusively for Windows and has no official support in alternative operating systems. BitLocker can utilize your PC's Trusted Platform Module (TPM) to store its encryption key secrets. In modern versions of Windows such as Windows 8.1 and Windows 10, BitLocker supports hardware-accelerated encryption if certain requirements are met (the drive has to support it, Secure Boot must be on and many other requirements). Without hardware encryption, BitLocker switches to software-based encryption so there is a dip in your drive's performance. BitLocker in Windows 10 supports a number of encryption methods, and supports changing a cipher strength.
Note: In Windows 10, BitLocker Drive Encryption is only available in the Pro, Enterprise, and Education editions. BitLocker can encrypt the system drive (the drive Windows is installed on), and internal hard drives. The BitLocker To Go feature allows protecting files stored on a removable drives, such as a USB flash drive.
Windows 10 includes a special Group Policy that, when enabled, denies write Access to Removable disks not protected by BitLocker. All removable data drives that are not BitLocker-protected will be accessible as read-only. If a drive is protected by BitLocker, it will be mounted with read and write access.
If you need to apply a restriction and prevent users from having write access to removable drives not protected by BitLocker, Windows 10 offers you at least two methods, a Group Policy option, and a Group Policy Registry tweak. The first method can be used in editions of Windows 10 that come with the Local Group Policy Editor app. If you are running Windows 10 Pro, Enterprise, or Education edition, then the Local Group Policy Editor app is available in the OS out of the box. Windows 10 Home users can apply a Registry tweak. Let's review these methods.
Deny Write Access to Removable Drives not Protected by BitLocker,
- Open the Local Group Policy editor app, or launch it for all users except Administrator, or for a specif user.
- Navigate to Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Removable Data Drives on the left.
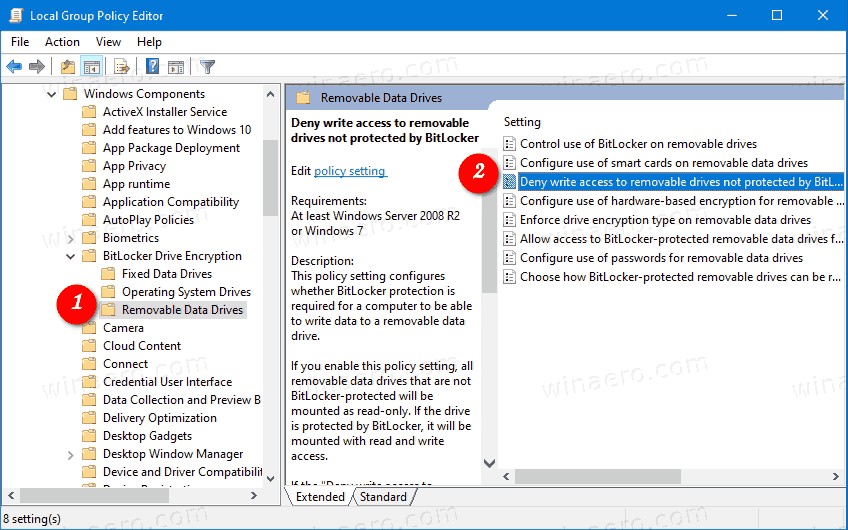
- On the right, find the policy setting Deny write access to removable drives not protected by BitLocker.
- Double-click on it and set the policy to Enabled.
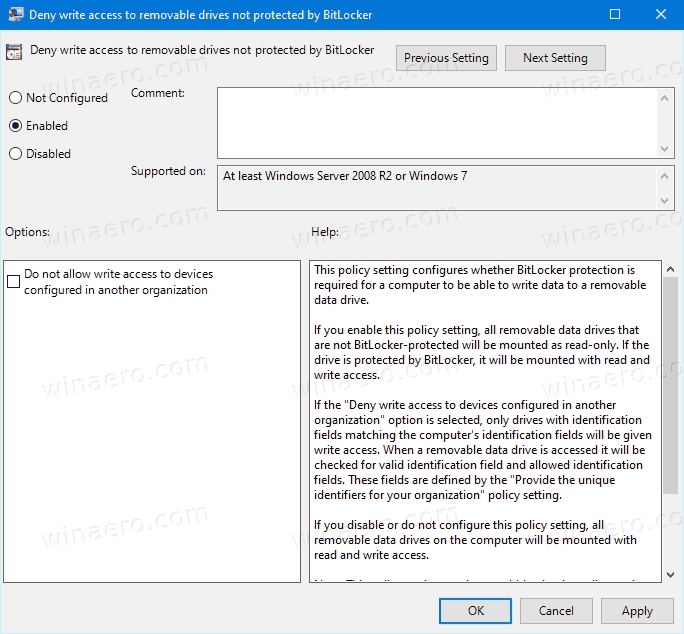
- If the Deny write access to devices configured in another organization option is enabled, only drives with identification fields matching the computer's identification fields will be available for writing.
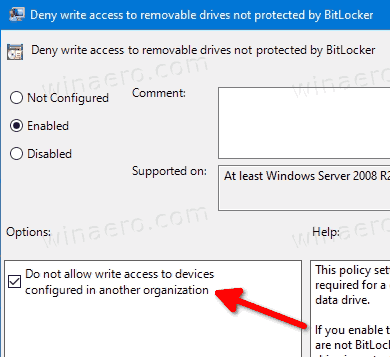
You are done. If someone tries to write on a removable drive not protected by BitLocker, he will be prompted to encrypt it first. Otherwise, the operation will be cancelled.
Tip: See How to Reset All Local Group Policy Settings at once in Windows 10.
Now, let's see how the same can be done with a Registry tweak.
Disable Write Access to Removable Disks with a Registry Tweak
- Open Registry Editor.
- Go to the following Registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Policies\Microsoft\FVE. Tip: See how to jump to the desired Registry key with one click. If you do not have such a key, then just create it. - Here, create a new 32-bit DWORD value
RDVDenyWriteAccess. Note: Even if you are running 64-bit Windows, you still need to use a 32-bit DWORD as the value type.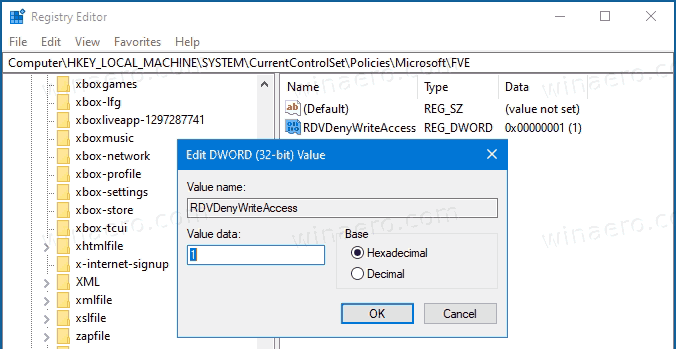
- Set it to 1 to disable the write access.
- If you want to enable the Deny write access to devices configured in another organization option, navigate to the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE. - Here, create a new 32-bit DWORD value
RDVDenyCrossOrg, and set it to 1.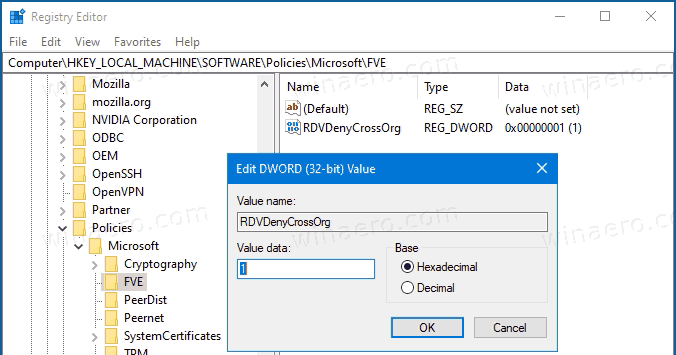
- Delete both values to restore defaults.
- To make the changes done by the Registry tweak take effect, restart Windows 10.
Interested users can download the ready-to-use Registry files:
The undo tweak is included.
Tip: You can try to enable GpEdit.msc in Windows 10 Home.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
