You can now enable Encrypted Client Hello in Microsoft Edge, starting in version 105. After that, the browser will encrypt all parameters of the TLS protocol, making connections more secure.
Advertisеment
TLS stands for Transport Layer Security, a widely used protocol that protects data transmitted between a web app and its server. For example, it is used when the browser loads a web site. TLS is core part of HTTPS, but also used in emails, VoIP, and modern instant messaging.
TLS provides privacy and confidentiality integrity, and authenticity based on certificates. It has a history of several versions and implementations, with the actual and the most secure one of them is TLS 1.3.
Encrypted Client Hello (ECH) is an extension of the TLS 1.3 protocol that encrypts the earlier connection stage. A web server on the Internet can serve several domains/websites from the same IP address, which is very common on virtual and shared hosting.
The browser establishes a TLS connection before HTTPS, so it needs to know the exact server name. To avoid server name interception and data manipulation, ECH encrypts the whole payload with a public key known to the browser. Encrypted Client Hello also requires DNS-over-HTTPS.
The current ECH protocol extension exists since 2020, and can be enabled in Firefox. Now Edge follows the suit and allows you enabling ECH. It is still an experimental feature available in Edge 105, and requires you to work with flags and the enable-feature argument. Note that as of now, Edge 105 is in the Dev and Beta, and version 106 is in the Canary channel. It doesn't yet work in Edge 106! Use either Beta or Dev build.
To enable the Encrypted Client Hello in Microsoft Edge, do the following.
How to Enable Encrypted Client Hello in Edge
- Right-click the Edge shortcut on the desktop, and select Properties from the menu.
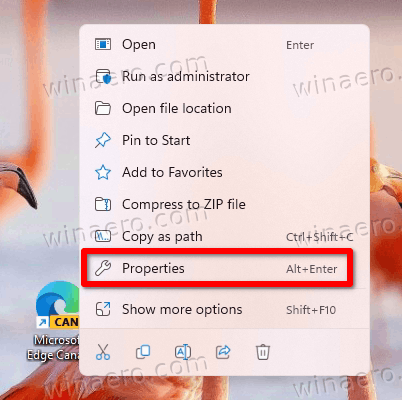
- Paste
--enable-features=EncryptedClientHelloafter "C:\..\msedge.exe" in the Target text box.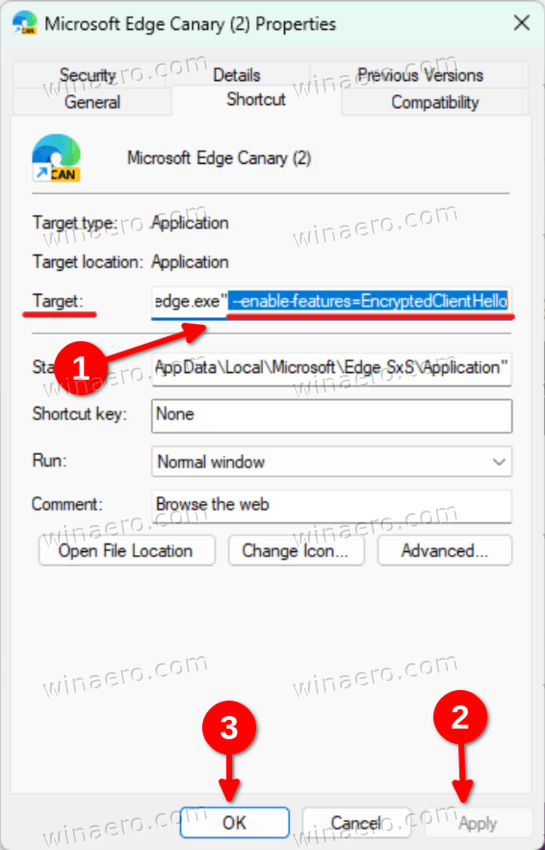
- Click Apply and OK.
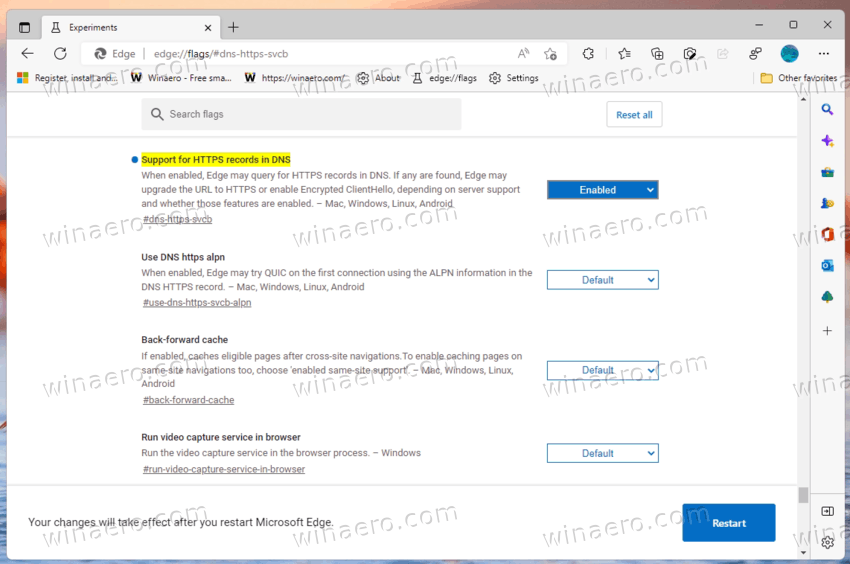
- Launch Edge using the modified shortcut, and type or copy-paste edge://flags/#dns-https-svcb into the address bar.
- Select Enabled from the drop-down list for the Support for HTTPS records in DNS.
- Similarly, enable the edge://flags/#use-dns-https-svcb-alpn flag, and relaunch the browser using the button below.
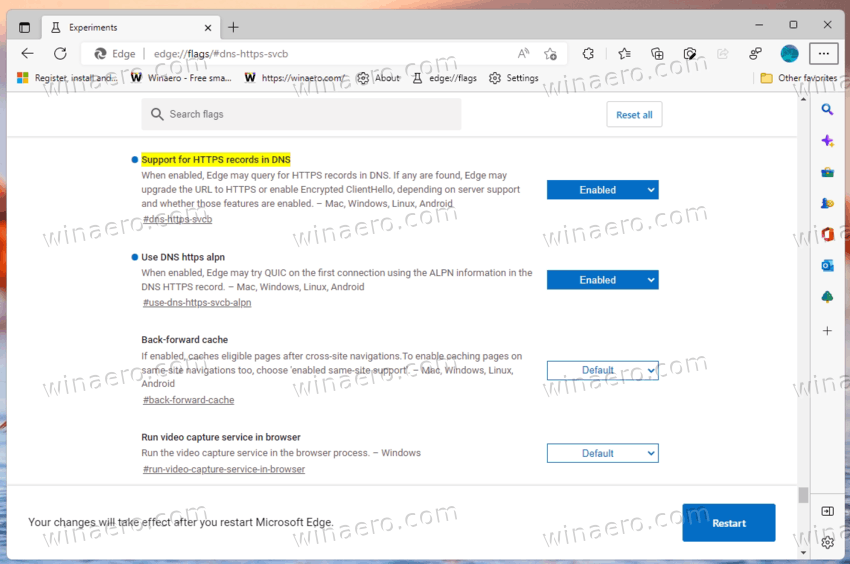
- Finally, open Edge menu (Alt + F), and go to Settings > Privacy, search, and services.
- Under Security, enable Use secure DNS, and select Cloudflare from the list of available providers.
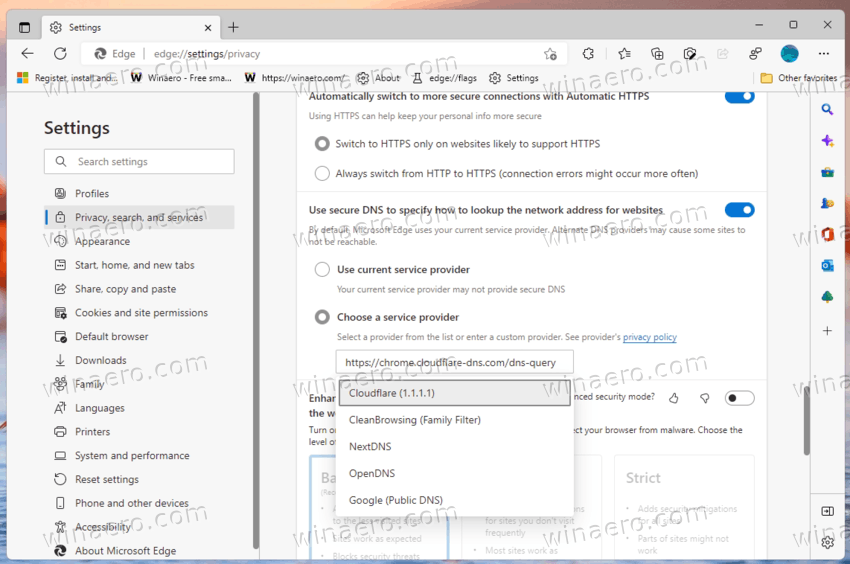
- Restart the browser one more time.
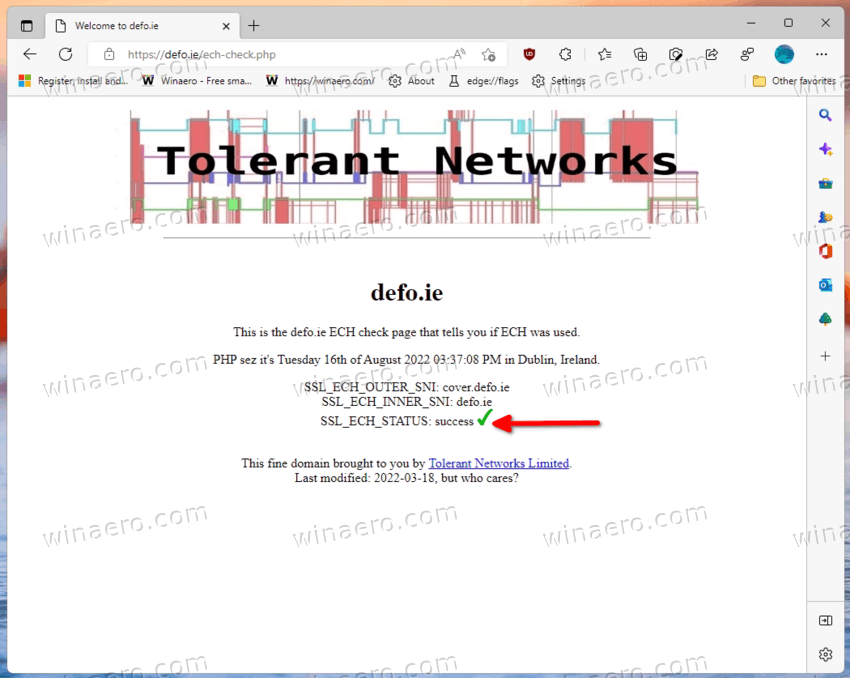
You are done. You now have the ECH protocol extension enabled in your browser. To ensure it works properly, you can use the following web page:
https://defo.ie/ech-check.php
Open it in your Edge browser and see the status for the SSL_ECH params.
So, Encrypted Client Hello is a work-in-progress on the whole Chromium platform. If you are interested in learning more about its development, you can track it here. Once it will become stable, it will be available out of the box in public versions of Chrome, Edge and other Chromium-based browsers.
Via TechCommunity
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
