Yesterday, a vulnerablity was discovered in the hardware encryption implemented by some SSDs. Unfortunately, BitLocker in Windows 10 (and possibly Windows 8.1 as well) delegates the duty of securely encrypting and protecting the user's data to the drive manufacturer. When hardware encryption is available, it does not verify if the encryption is foolproof, and turns off its own software-based encryption, making your data vulnerable. Here is a workaround you can apply.
Advertisеment

Even if you enable BitLocker encryption on a system, Windows 10 may not be actually encrypting your data with its software encryption if the drive conveys to the operating system that it is using hardware encryption. Even if your disk drive supports encryption, it may be easily broken due to the use of a blank passphrase.
A recent study shows that Crucial and Samsung products have plenty of issues with their SSDs. For instance, certain Crucial models have an empty master password, allowing access to the encryption keys. It is quite possible that the firmware used in other hardware by various vendors may also have similar issues.
As a workaround, Microsoft suggests disabling hardware encryption and switching to BitLocker's software encryption if you have really sensitive and important data.
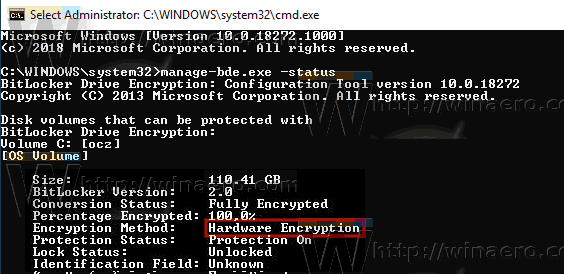
First of all, you need to check which type of encryption your system is currently using.
Check Status of BitLocker Drive Encryption for Drive in Windows 10
- Open an elevated command prompt.
- Type or copy-paste the following command:
manage-bde.exe -status
- See the line 'Encryption Method'. If it contains 'Hardware Encryption', then BitLocker relies on hardware encryption. Otherwise it is using software encryption.
Here is how to switch from hardware encryption to software encryption with BitLocker.
Disable Hardware BitLocker Encryption
- Fully turn off BitLocker to decrypt the drive.
- Open PowerShell as Administrator.
- Issue the command:
Enable-BitLocker -HardwareEncryption:$False - Enable BitLocker again.
If you are a system administrator, enable and deploy the policy 'Configure use of hardware-based encryption for operating system drives'.
Disable Hardware BitLocker Encryption with Group Policy
If you are running Windows 10 Pro, Enterprise, or Education edition, you can use the Local Group Policy Editor app to configure the options mentioned above with a GUI.
- Press Win + R keys together on your keyboard and type:
gpedit.msc
- Group Policy Editor will open. Go to Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives. Set the policy optionConfigure use of hardware-based encryption for operating system drives to Disabled.
Alternatively, you can apply a Registry tweak.
Disable Hardware BitLocker Encryption with Registry Tweak
- Open Registry Editor.
- Go to the following Registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE
Tip: See how to jump to the desired Registry key with one click.
If you do not have such a key, then just create it.
- Here, create a new 32-bit DWORD value OSAllowedHardwareEncryptionAlgorithms. Note: Even if you are running 64-bit Windows, you still need to use a 32-bit DWORD as the value type.
Leave its value data as 0. - To make the changes done by the Registry tweak take effect, restart Windows 10.
That's it.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options: