Meta and Yandex secretly tracked users and bypassed privacy tools like incognito mode and cookie-clearing features. They used a technique called session deanonymization on Android devices when users visited websites that used Yandex Metrica or Facebook Pixel analytics.
Advertisеment
How the Tracking Worked
The method worked by using mobile apps like Facebook, Instagram, Yandex Maps, Yandex Navigator, Yandex Search, Yandex Go, and Yandex Browser to create a hidden communication link with JavaScript running in browsers. These apps set up connection handlers on the local network (127.0.0.1) and accepted requests through HTTP, HTTPS, WebSocket, and WebRTC protocols.
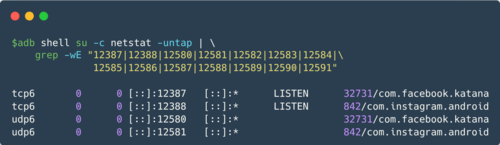
When users visited websites with Yandex Metrica or Facebook Pixel, the JavaScript sent requests to network ports opened by the mobile apps. These requests carried metadata, cookies, and control commands. The apps then linked browser activity to real user and device identifiers, such as Facebook or Yandex accounts or AAID (Android Advertising ID). This allowed Meta and Yandex to identify users even if they used incognito mode or deleted cookies, by matching browser activity with identifiers from the apps running on the same device.
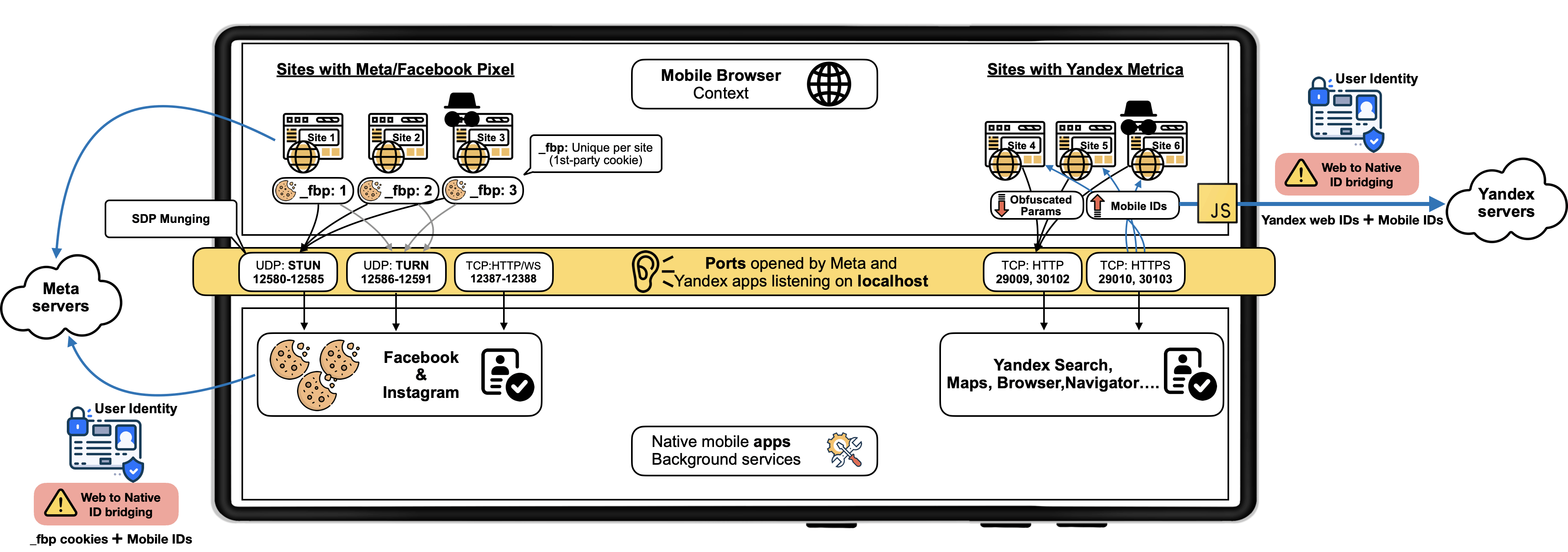
Exploiting Android's Weaknesses
Meta and Yandex took advantage of Android's lack of restrictions on creating listening sockets tied to the loopback interface (127.0.0.1) for apps with internet permissions. For Facebook, the app grabbed the "_fbp" cookie, a unique user identifier in Facebook Pixel. By manipulating WebRTC, this data was inserted into the "ice-ufrag" field of SDP packets sent to localhost. On May 17, Chrome blocked this feature, and Facebook Pixel scripts switched to using WebRTC TURN. After the issue was exposed, Meta stopped sending requests to localhost in Facebook Pixel scripts.
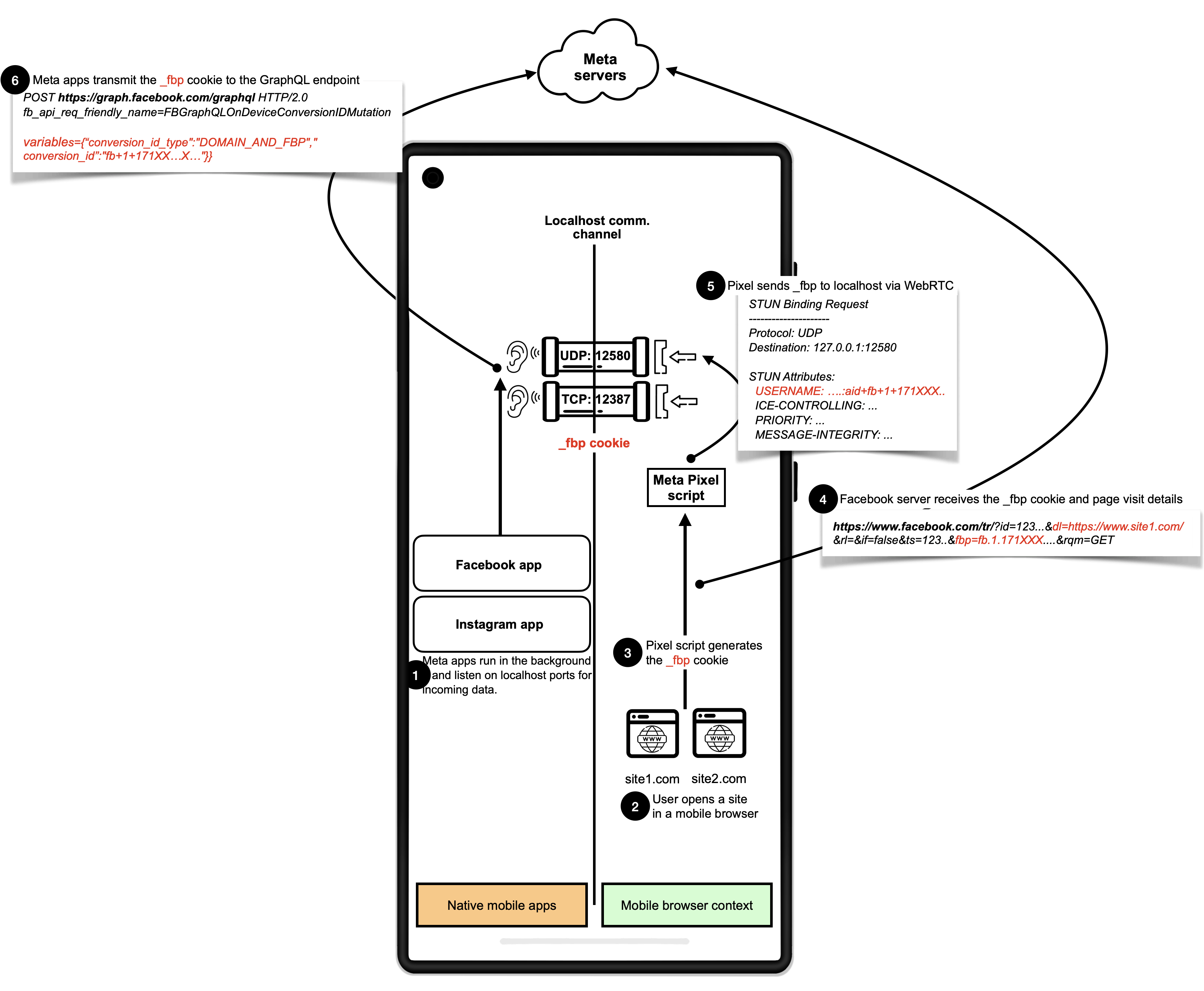
Risks of the Technique
This technique was risky not only because it leaked data to Facebook and Yandex but also because malicious apps could exploit the open network ports to track users and build browsing histories, going beyond what Facebook and Yandex intended.
Yandex's Long-Standing Method
Yandex had been using this method since 2017. The JavaScript in Yandex Metrica created HTTP or HTTPS connections to localhost on specific network ports (29009, 29010, 30102, and 30103). Requests were sent to yandexmetrica.com, which resolved to the IP address 127.0.0.1. Information about the ports where Yandex apps needed to listen for connections was loaded dynamically through requests to startup.mobile.yandex.net.
The server also sent a parameter called "first_delay_seconds," which set a delay before the apps started accepting connections. Apps began listening about three days after installation instead of immediately. When the apps received HTTP requests, they sent back data including Yandex service identifiers, system UUIDs, and AAID. Yandex Metrica's JavaScript then forwarded these identifiers to the mc.yango.com server.
Browser Compatibility
These methods worked in Android versions of Chrome and Edge. In Firefox, only Yandex’s method functioned. DuckDuckGo and Brave either blocked requests to localhost or required manual approval. Chrome 137, released in late May, added protection against data substitution in SDP.
Efforts to Prevent Users deanonymization
To prevent such abuses, a new specification called PNA (Private Network Access) is being developed. It aims to limit access to internal network hosts (e.g., 127.0.0.0/8, 192.168.0.0/16, 10.0.0.0/8). A trial version in Chrome faced compatibility issues with some devices. Currently, a second version, LNA (Local Network Access), is being worked on. This version avoids requiring changes on the device side and focuses on adjustments to websites that need access to internal network resources.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
