In a recent security advisory, Microsoft has issued a warning that certain Secure Boot certificates will expire. These certificates were originally issued in 2011 and are mandatory to the integrity of the system boot process. The company strongly recommends users and organizations to check and update their systems before the expiration date.
Secure Boot Mechanism Overview
Secure Boot, first introduced with Windows 8 in 2012, is a UEFI-based security standard designed to verify firmware integrity and ensure that only trusted components are loaded during the operating system startup sequence. It plays a critical role in preventing unauthorized code from executing at boot time and is required for official installation of modern Windows editions, including Windows 10, Windows 11, and various Windows Server releases.
Advertisеment
At the manufacturing stage, certificates of trusted certification authorities are installed on the motherboard. When the SecureBoot option is enabled, the trust of the certificate that signs the downloaded binary is checked.
Not only Windows components are signed in this way, but also boot managers, Linux kernels of many distributions, etc., but it is actually configured and used mainly in the case of a pre-installed OS.
The package with new certificates of certification centers for SecureBoot must be signed by certificates of valid (known to the EFI firmware) certification centers. Windows, in addition to updating itself, also updates certificates (and lists of certificate revocations) of certification centers for SecureBoot.
The upcoming expiration applies to systems running Windows 10, Windows 11, Windows Server 2012 through Windows Server 2025, both physical and virtual machines. Devices manufactured in 2025 or later, including Copilot+ PCs, are not affected by this issue, as they ship with newer certificate sets.
Potential Risks of Expired Certificates
If updated certificates are not applied prior to expiration, systems may no longer receive critical security updates for the Windows Boot Manager and related Secure Boot components. Moreover, Secure Boot depends on the validity of those certificates. If the certificate in the bootmgfw.efi file on the UEFI partition is invalid and unknown to the non-updated EFI, the device will not start with Secure Boot enabled.
This can expose devices to advanced persistent threats, such as bootkit malware, which operates outside the scope of traditional antivirus detection methods. Notably, malware such as BlackLotus has exploited outdated Secure Boot configurations to gain deep system access without user awareness.
Recommended Actions for Affected Systems
Microsoft advises users and IT administrators to proactively update Secure Boot certificates by applying monthly cumulative updates, which will include new certificates starting in the coming months. Organizations using legacy Windows 10 deployments are encouraged to enroll in the Extended Security Updates program to continue receiving critical patches beyond the mainstream support period. This program is offered free of charge to consumer users.
For dual-boot environments involving Linux and Windows, Microsoft states it will provide updated certificates compatible with cross-platform configurations, ensuring continued interoperability while preserving system integrity.
In short, you are limited to these solutions.
- It is necessary to install current updates on your hardware in the next year for Windows installed in EFI mode.
- Install motherboard firmware updates.
- do not use SecureBoot with modern OS if the first two steps can't be done.
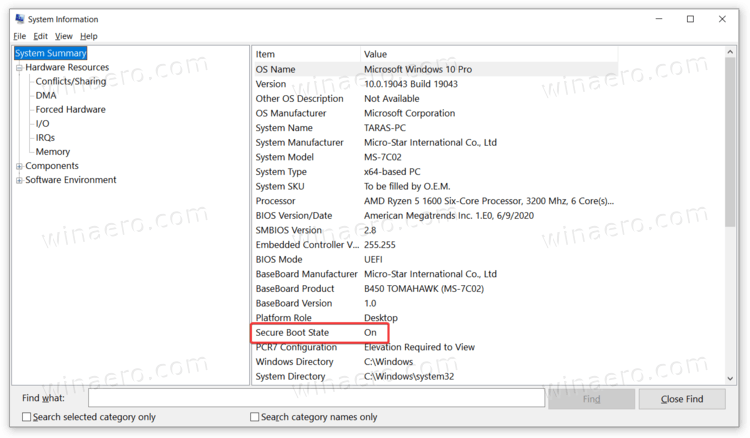
How to Check Secure Boot Status
To verify whether Secure Boot is enabled and functioning correctly, users may press Win + R, type msinfo32, and check the value listed under Secure Boot Status. A status of “Enabled” indicates that the feature is active and properly configured.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

How and from where to update?
Start from device vendor’s website.