Google has released a new version of the Chrome browser to the stable branch. Chrome 84 is a maintenance release that fixes a number of security vulnerabilities, and also includes a few improvements.
Google Chrome is the most popular web browser which exists for all major platforms like Windows, Android and Linux. It comes with a powerful rendering engine which supports all modern web standards.

Version 84 of the browser is notable for resolving 38 security issues. Here are some highlights: Show/Hide
[$TBD][
1103195] Critical CVE-2020-6510: Heap buffer overflow in background fetch. Reported by Leecraso and Guang Gong of 360 Alpha Lab working with 360 BugCloud on 2020-07-08
[$5000][
1074317] High CVE-2020-6511: Side-channel information leakage in content security policy. Reported by Mikhail Oblozhikhin on 2020-04-24
[$5000][
1084820] High CVE-2020-6512: Type Confusion in V8. Reported by nocma, leogan, cheneyxu of WeChat Open Platform Security Team on 2020-05-20
[$2000][
1091404] High CVE-2020-6513: Heap buffer overflow in PDFium. Reported by Aleksandar Nikolic of Cisco Talos on 2020-06-04
[$TBD][
1076703] High CVE-2020-6514: Inappropriate implementation in WebRTC. Reported by Natalie Silvanovich of Google Project Zero on 2020-04-30
[$TBD][
1082755] High CVE-2020-6515: Use after free in tab strip. Reported by DDV_UA on 2020-05-14
[$TBD][
1092449] High CVE-2020-6516: Policy bypass in CORS. Reported by Yongke Wang of Tencent's Xuanwu Lab (xlab.tencent.com) on 2020-06-08
[$TBD][
1095560] High CVE-2020-6517: Heap buffer overflow in history. Reported by ZeKai Wu (@hellowuzekai) of Tencent Security Xuanwu Lab on 2020-06-16
[$3000][
986051] Medium CVE-2020-6518: Use after free in developer tools. Reported by David Erceg on 2019-07-20
[$3000][
1064676] Medium CVE-2020-6519: Policy bypass in CSP. Reported by Gal Weizman (@WeizmanGal) of PerimeterX on 2020-03-25
[$1000][
1092274] Medium CVE-2020-6520: Heap buffer overflow in Skia. Reported by Zhen Zhou of NSFOCUS Security Team on 2020-06-08
[$500][
1075734] Medium CVE-2020-6521: Side-channel information leakage in autofill. Reported by Xu Lin (University of Illinois at Chicago), Panagiotis Ilia (University of Illinois at Chicago), Jason Polakis (University of Illinois at Chicago) on 2020-04-27
[$TBD][
1052093] Medium CVE-2020-6522: Inappropriate implementation in external protocol handlers. Reported by Eric Lawrence of Microsoft on 2020-02-13
[$N/A][
1080481] Medium CVE-2020-6523: Out of bounds write in Skia. Reported by Liu Wei and Wu Zekai of Tencent Security Xuanwu Lab on 2020-05-08
[$N/A][
1081722] Medium CVE-2020-6524: Heap buffer overflow in WebAudio. Reported by Sung Ta (@Mipu94) of SEFCOM Lab, Arizona State University on 2020-05-12
[$N/A][
1091670] Medium CVE-2020-6525: Heap buffer overflow in Skia. Reported by Zhen Zhou of NSFOCUS Security Team on 2020-06-05
[$1000][
1074340] Low CVE-2020-6526: Inappropriate implementation in iframe sandbox. Reported by Jonathan Kingston on 2020-04-24
[$500][
992698] Low CVE-2020-6527: Insufficient policy enforcement in CSP. Reported by Zhong Zhaochen of andsecurity.cn on 2019-08-10
[$500][
1063690] Low CVE-2020-6528: Incorrect security UI in basic auth. Reported by Rayyan Bijoora on 2020-03-22
[$N/A][
978779] Low CVE-2020-6529: Inappropriate implementation in WebRTC. Reported by kaustubhvats7 on 2019-06-26
[$N/A][
1016278] Low CVE-2020-6530: Out of bounds memory access in developer tools. Reported by myvyang on 2019-10-21
[$TBD][
1042986] Low CVE-2020-6531: Side-channel information leakage in scroll to text. Reported by Jun Kokatsu, Microsoft Browser Vulnerability Research on 2020-01-17
[$N/A][
1069964] Low CVE-2020-6533: Type Confusion in V8. Reported by Avihay Cohen @ SeraphicAlgorithms on 2020-04-11
[$N/A][
1072412] Low CVE-2020-6534: Heap buffer overflow in WebRTC. Reported by Anonymous on 2020-04-20
[$TBD][
1073409] Low CVE-2020-6535: Insufficient data validation in WebUI. Reported by Jun Kokatsu, Microsoft Browser Vulnerability Research on 2020-04-22
[$TBD][
1080934] Low CVE-2020-6536: Incorrect security UI in PWAs. Reported by Zhiyang Zeng of Tencent security platform department on 2020-05-09
Improvements in Chrome 84
- Google continues to roll out the SameSite cookie restriction. The process was suspended in Chrome 80. Chrome is enforcing secure-by-default handling of third-party cookies as part of our ongoing effort to improve privacy and security across the web.
- TLS 1.0 and TLS 1.1 are deprecated starting in Chrome 84. Both protocols can still be used in Chrome 84, but will be removed in the future.
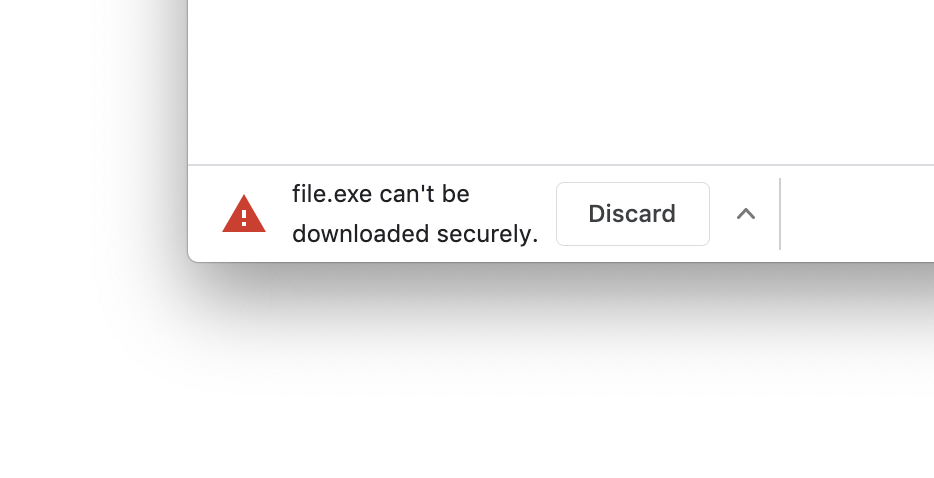
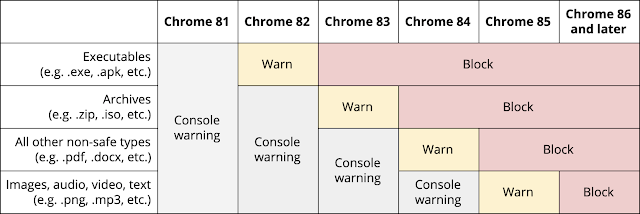
- Users will get a warning in the developer console about insecure downloads via the plain HTTP.
- Chrome will suppress abusive web notifications starting in version 84.
Download Links
Web installer: Google Chrome 64-bit
MSI/Enterprise installer: Google Chrome MSI Installers for Windows
Note: The offline installer doesn't support the automatic update feature of Chrome. By installing it this way, you will be forced to always update your browser manually.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won't take a lot from you, but it will help us grow. Thanks for your support!
Author: Sergey Tkachenko
Sergey Tkachenko is a software developer who started Winaero back in 2011. On this blog, Sergey is writing about everything connected to Microsoft, Windows and popular software. Follow him on Telegram, Twitter, and YouTube. View all posts by Sergey Tkachenko



