Last week Google released Chrome 125, a major release and the first one with native ARM64 builds. Besides, there is now in-depth executable file scan that runs automatically, an extra warning for add-ons installed outside of the Web Store, and a few more changes.

What's new in Chrome 125
Google has again postponed the support removal for third-party cookies set when accessing sites other than the domain of the current page. Such cookies are used to track user navigation between sites via advertising blocks, social networking widgets and web analytics systems.
Advertisеment
In this new version, to identify sites that use third-party Cookies, Google has added an indicator with an eye that appears in the address bar, which is crossed out when third-party Cookies are blocked.
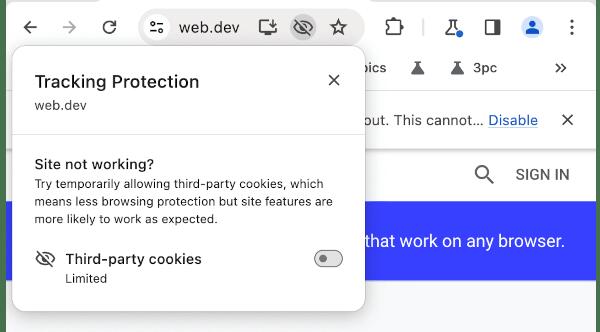
The company continues testing of disabling third-party cookies on 1% of users. Interested users can manually disable them via the "chrome://flags/#test-third-party-cookie-phaseout" setting. Also, the context menu provides the ability to temporarily restore third-party cookies support for selected sites. They will be enabled for 90 days after activation.
Scanning of downloaded files
When you enable enhanced browser protection (Safe Browsing > Enhanced protection), Chrome will run automatic deep scanning of downloaded files. It will be done by uploading information to Google servers. Previously, before sending, a request was displayed to confirm external verification, but now the verification will be performed automatically.
ARM64 Support
Builds for the Windows platform are now available for the ARM64 platform.
Other changes
- A new mechanism has been added for updating components that require loading a large amount of data. It will be used for updating models for recently added features using machine learning - smart tab grouping mode, theme generator and interactive assistant.
- Added two new types of potentially problematic add-ons that will prompt users to think about their continued use: add-ons not installed from the Chrome Web Store, and add-ons that use deceptive tactics to force installation of unnecessary software.
In addition to new features and bug fixes, the new version closes 9 vulnerabilities. Many of the vulnerabilities were identified as a result of automated testing using the AddressSanitizer, MemorySanitizer, Control Flow Integrity , LibFuzzer and AFL tools.
The vulnerability CVE-2024-4947, caused by incorrect handling of types (Type Confusion) in the V8 engine and classified as dangerous, was used by attackers to carry out zero-day attacks before being fixed. Google has not yet disclosed details on this vulnerability, but independent researchers have analyzed and published technical details, as well as a prototype of the exploit.
No critical problems have been identified that would allow one to bypass all levels of browser protection and execute code on the system outside the sandbox environment. As part of the bug bounty program, Google paid 4 awards in the amount of 8 thousand US dollars (one award each of $7000, $1000). The size of the two rewards has not yet been determined.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
