As you may already know, all Intel CPUs released during the past decade, ARM64 CPUs and certain AMD CPUs are affected by a serious issue. A specially malformed code can be used to steal the private data of any other process, including sensitive data like passwords, security keys and so on. Even a browser with JavaScript enabled can be used as an attack vector. If you are an Opera user, you can do the following.
Advertisеment
If you are not aware about the Meltdown and Spectre vulnerabilities, we have covered them in detail in these two articles:
- Microsoft is rolling out emergency fix for Meltdown and Spectre CPU flaws
- Here are Windows 7 and 8.1 fixes for Meltdown and Spectre CPU flaws
In short, both Meltdown and Spectre vulnerabilities allow a process to read the private data of any other process, even from outside a virtual machine. This is possible due to Intel's implementation of how their CPUs prefetch data. This cannot be fixed by patching the OS only. The fix involves updating the OS kernel, as well as a CPU microcode update and possibly even a UEFI/BIOS/firmware update for some devices, to fully mitigate the exploits.
The attack can be performed with only JavaScript too using a browser.
Opera is a Chromium-based web browser. Its origins can be found in Norway, now it is owned by a Chinese company. Prior to version 12, the browser had its own rendering engine, Presto, which was ditched in favor of Blink.
Google is going to add extra protection against the mentioned vulnerabilities to Chromium version 64. After that, an updated version of Opera will use it in order to protect the users.
Currently, you can enable Full Site Isolation manually in Opera for protection against the mentioned vulnerabilities.
What is Full Site Isolation
Site Isolation is a security feature in the Chromium engine that offers additional protection against some types of security bugs. It makes it harder for untrusted websites to access or steal information from your accounts on other websites.
Websites typically cannot access each other's data inside the browser, thanks to code that enforces the Same Origin Policy. Occasionally, security bugs are found in this code and malicious websites may try to bypass these rules to attack other websites. The Chrome team aims to fix such bugs as quickly as possible.
Site Isolation offers a second line of defense to make such vulnerabilities less likely to succeed. It ensures that pages from different websites are always put into different processes, each running in a sandbox that limits what the process is allowed to do. It also blocks the process from receiving certain types of sensitive documents from other sites. As a result, a malicious website will find it more difficult to steal data from other sites, even if it can break some of the rules in its own process.
Recently, I wrote how to enable Full Site Isolation in Google Chrome. The same can be done for Opera.
Secure Opera Against Meltdown and Spectre vulnerabilities
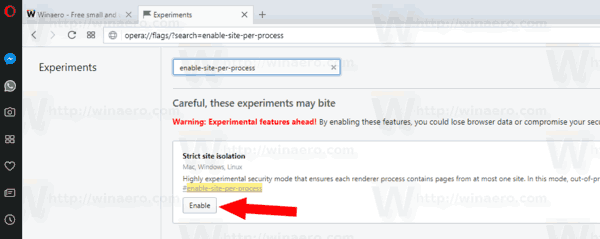
- Open Opera.
- Type
opera://flags/?search=enable-site-per-processin the address bar. - Enable the flag "Strict site isolation" using the button next to the flag description.
Note that enabling Full Site Isolation will increase memory usage - it can be 10%-20% more than usual.
It is worth mentioning that Firefox is using a different protection mechanism. If you are a Firefox user, please refer to the following article:
Firefox 57.0.4 released with Meltdown and Spectre attack workaround
That's it.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Doesn’t work, tested with tencent’s spectre check website
xlab tencent com / special / spectre /spectre_check html