It is no secret any more that all Intel CPUs released during the past decade are affected by a serious issue. A specially malformed code can be used to steal the private data of any other process, including sensitive data like passwords, security keys and so on. In this article, we will see how to find if your PC is affected by the issue.
Advertisеment
If you are not aware about the Meltdown and Spectre vulnerabilities, we have covered them in detail in these two articles:
- Microsoft is rolling out emergency fix for Meltdown and Spectre CPU flaws
- Here are Windows 7 and 8.1 fixes for Meltdown and Spectre CPU flaws
In short, both Meltdown and Spectre vulnerabilities allow a process to read the private data of any other process, even from outside a virtual machine. This is possible due to Intel's implementation of how their CPUs prefetch data. This cannot be fixed by patching the OS only. The fix involves updating the OS kernel, as well as a CPU microcode update and possibly even a UEFI/BIOS/firmware update for some devices, to fully mitigate the exploits.
Recent research indicates that ARM64 and AMD CPUs are affected as well by the Spectre vulnerability, related to speculative execution.
Available fixes
Microsoft has already released a set of fixes for all supported operating systems. Mozilla today issued an updated version of Firefox 57, and Google will protect Chrome users with version 64.
For the current version Google Chrome, you can enable extra protection by enabling Full Site Isolation. Site Isolation offers a second line of defense to make such vulnerabilities less likely to succeed. It ensures that pages from different websites are always put into different processes, each running in a sandbox that limits what the process is allowed to do. It also blocks the process from receiving certain types of sensitive documents from other sites.
Google will update Chrome again (Version 64) by the end of the month to protect against exploitation of vulnerabilities related to Meltdown and Spectre. Version 64 of Chrome has already arrived on the beta channel.
Find if your PC is affected by Meltdown and Spectre vulnerabilities
Note: The instructions below are applicable to Windows 10, Windows 8.1 and Windows 7 SP1.
- Open PowerShell as administrator.
- Type the following command:
Install-Module SpeculationControl. This will install an extra module on your computer. Answer "Y" twice.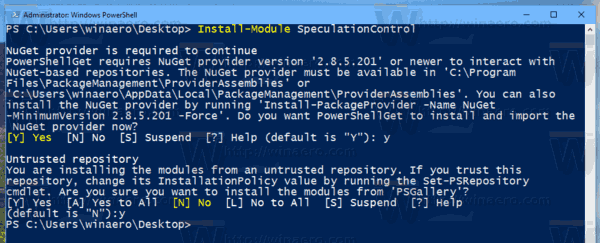
- Activate the installed module with the command:
Import-Module SpeculationControl. - Now, execute the following cmdlet:
Get-SpeculationControlSettings. - In the output, see the enabled protections shown as "True".
Note: If you are getting the error message
"Import-Module : File C:\Program Files\WindowsPowerShell\Modules\SpeculationControl\1.0.1\SpeculationControl.psm1
cannot be loaded because running scripts is disabled on this system. ..."
Then change execution policy to unrestricted or bypass. Refer to the following article:
How to Change PowerShell Execution Policy in Windows 10
You are protected if all lines have the True value. Here is how my unpatched Windows 10 appears in the output: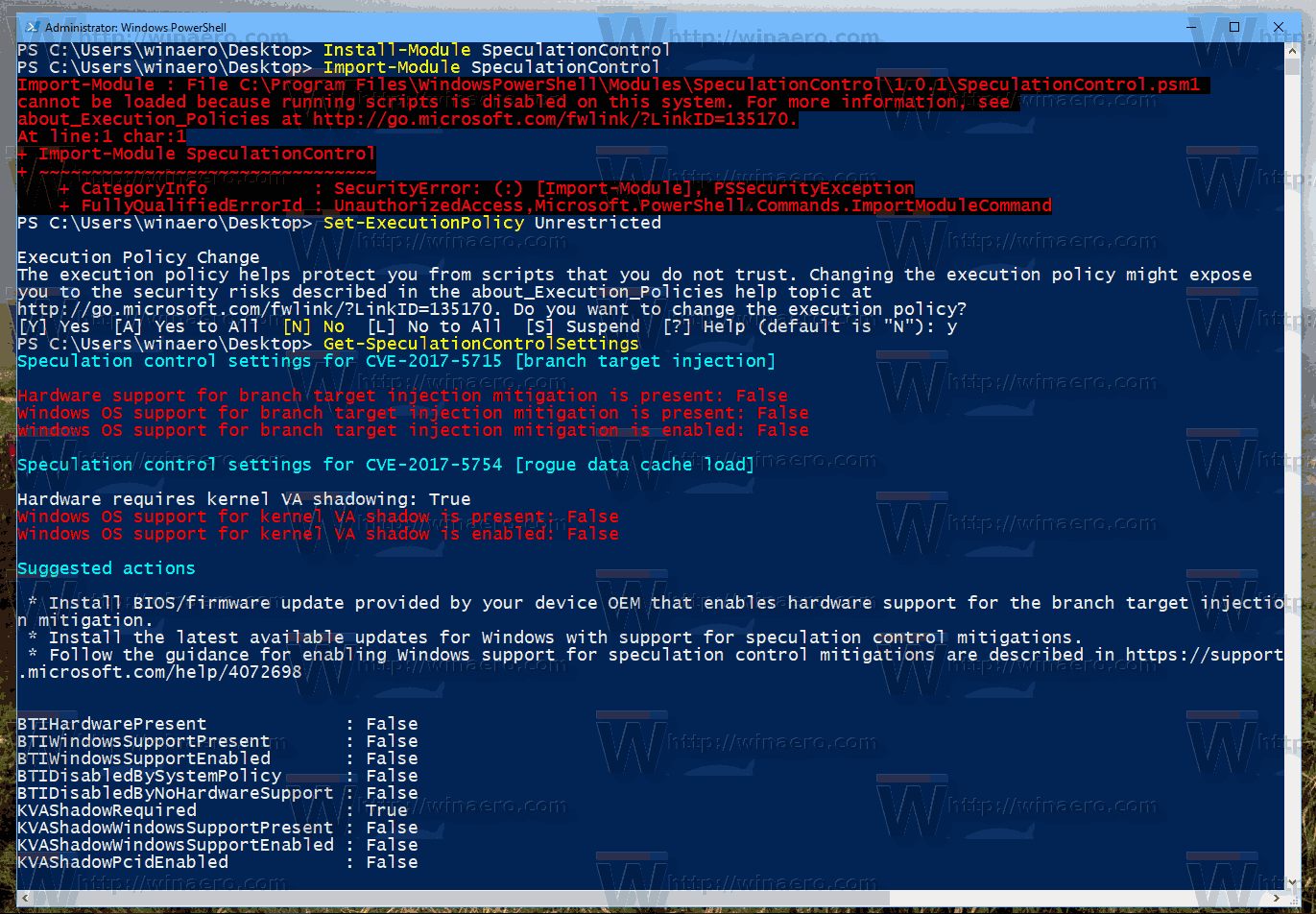
That's it.
Source: Microsoft
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Без знаний всё равно непонятно что смотреть
Speculation control settings for CVE-2017-5715 [branch target injection]
Hardware support for branch target injection mitigation is present: False
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: False
Windows OS support for branch target injection mitigation is disabled by system policy: False
Windows OS support for branch target injection mitigation is disabled by absence of hardware support: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: False [not required for security]
Suggested actions
* Install BIOS/firmware update provided by your device OEM that enables hardware support for the branch target injection mitigation.
BTIHardwarePresent : False
BTIWindowsSupportPresent : True
BTIWindowsSupportEnabled : False
BTIDisabledBySystemPolicy : False
BTIDisabledByNoHardwareSupport : True
KVAShadowRequired : True
KVAShadowWindowsSupportPresent : True
KVAShadowWindowsSupportEnabled : True
KVAShadowPcidEnabled : False
Чем больше True, тем лучше. Вот такой принцип.
Far as I got on a Lenovo laptop
System SKU LENOVO_MT_80NW_BU_idea_FM_Lenovo ideapad Y700 Touch-15ISK
Processor Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz, 2601 Mhz, 4 Core(s), 8 Logical Processor(s)
BIOS Version/Date LENOVO CDCN54WW, 6/13/2017
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: True [not required for security]
Suggested actions
* Install BIOS/firmware update provided by your device OEM that enables hardware support for the branch target injection mitigation.
BTIHardwarePresent : False
BTIWindowsSupportPresent : True
BTIWindowsSupportEnabled : False
BTIDisabledBySystemPolicy : False
BTIDisabledByNoHardwareSupport : True
KVAShadowRequired : True
KVAShadowWindowsSupportPresent : True
KVAShadowWindowsSupportEnabled : True
KVAShadowPcidEnabled : True
System SKU LENOVO_MT_80NW_BU_idea_FM_Lenovo ideapad Y700 Touch-15ISK
Processor Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz, 2601 Mhz, 4 Core(s), 8 Logical Processor(s)
BIOS Version/Date LENOVO CDCN54WW, 6/13/2017
PS C:\WINDOWS\system32> Get-SpeculationControlSettings
Speculation control settings for CVE-2017-5715 [branch target injection]
Hardware support for branch target injection mitigation is present: False
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: False
Windows OS support for branch target injection mitigation is disabled by system policy: False
Windows OS support for branch target injection mitigation is disabled by absence of hardware support: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: True [not required for security]
Suggested actions
* Install BIOS/firmware update provided by your device OEM that enables hardware support for the branch target injection mitigation.
BTIHardwarePresent : False
BTIWindowsSupportPresent : True
BTIWindowsSupportEnabled : False
BTIDisabledBySystemPolicy : False
BTIDisabledByNoHardwareSupport : True
KVAShadowRequired : True
KVAShadowWindowsSupportPresent : True
KVAShadowWindowsSupportEnabled : True
KVAShadowPcidEnabled : True
А какой смысл в этом цмдлете вообше?
Если патчи установлены на Windows, значит уже пропатчено всё. А если не установлены, тогда нужно установить на все уязвимые машины.
На относительно не новых машинах обновления биос всё равно уже не дождаться…
Thank you very much for your tutorials, keep rocking like this!!
Not all fixed Win10 Build 16299.192, and no Bios Update is avaible (HP Envy), so i have to be patient is good enough?
PS C:\WINDOWS\system32> get-speculationControlSettings
Speculation control settings for CVE-2017-5715 [branch target injection]
Hardware support for branch target injection mitigation is present: False
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: False
Windows OS support for branch target injection mitigation is disabled by system policy: False
Windows OS support for branch target injection mitigation is disabled by absence of hardware support: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: True [not required for security]
Suggested actions
* Install BIOS/firmware update provided by your device OEM that enables hardware support for the branch target injection mitigation.
BTIHardwarePresent : False
BTIWindowsSupportPresent : True
BTIWindowsSupportEnabled : False
BTIDisabledBySystemPolicy : False
BTIDisabledByNoHardwareSupport : True
KVAShadowRequired : True
KVAShadowWindowsSupportPresent : True
KVAShadowWindowsSupportEnabled : True
KVAShadowPcidEnabled : True
I can’t install the module SpeculationControl. I have Windows 8.1 x64 SL(RUS), PowerShell 4.0.
PC c:\windows\system32> Install-Module SpeculationControl
Install-Module : Имя “Install-Module” не распознано как имя командлета, функции, файла сценария или выполняемой програм
мы. Проверьте правильность написания имени, а также наличие и правильность пути, после чего повторите попытку…
What can I do?
Oleg, try to install this package:
https://www.microsoft.com/en-us/download/details.aspx?id=51451This package is for Windows 8.1 Pro & Enterprise only. My version is SL (Windows 7 Home analog).
Maybe this one? https://www.microsoft.com/en-us/download/details.aspx?id=50395
This package is also intended only for Windows 8.1 Pro and Enterprise.
How do I find out the version of the Microsoft .NET Framework installed on my Windows 8.1?
I installed the package WMF 5.1. The question is removed.
Great!