Recently, Microsoft updated Microsoft Defender to version 4.18.2008.9, and also added new features to its console management tool, MpCmdRun.exe. Now it can be used to download any file from the Internet.
The console MpCmdRun.exe utility is part of Microsoft Defender. It is used mostly for scheduled scanning tasks by IT administrators. The MpCmdRun.exe tool has a number of command line switches which can be viewed by running MpCmdRun.exe with "/?".
The most recent version of the MpCmdRun.exe tool supports the following syntax
MpCmdRun.exe -DownloadFile -url [url to a remote file] -path [local path to save the file]
And this really works. The researcher @mohammadaskar2, who noticed the presence of the option, has demoed the use of MpCmdRun.exe to download a file from the Internet.
To reproduce his experience, navigate to the C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2008.9-0 folder (adjust the platform version if needed).
There, open a new command prompt, and type above command.
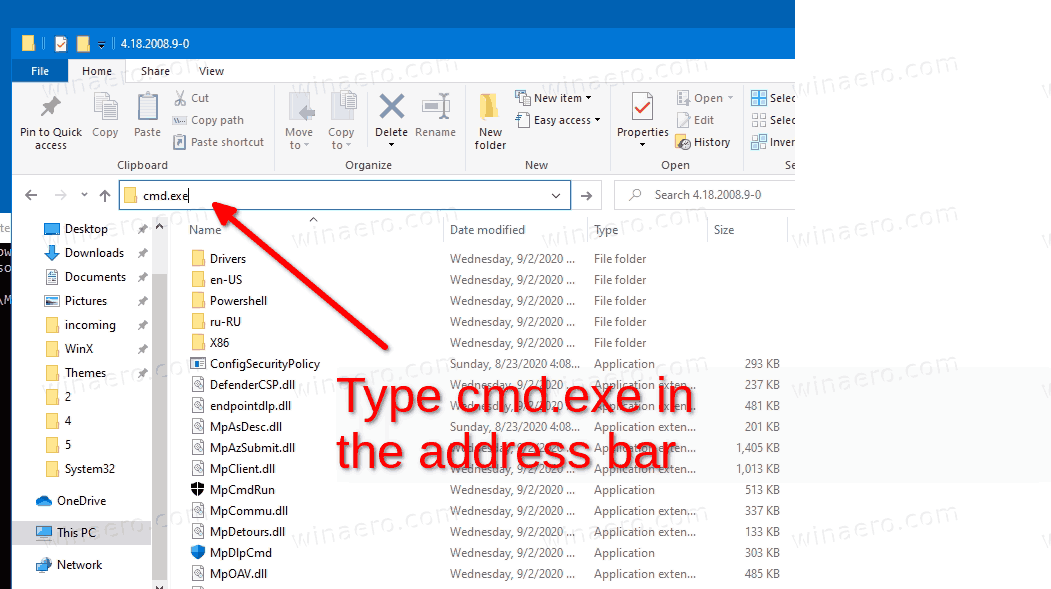
Provide the URL to the file you want to download, and the actual local path to the file you want to save the downloaded file to.
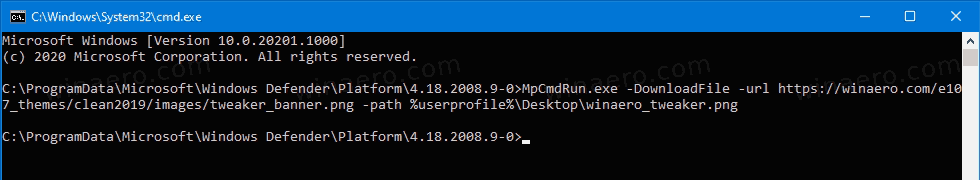
It will be silently downloaded to the location you specified.
Thanks to Roman Linev for sending the tip.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Okay, thanks ! How do you disable it ?
I don’t think that it is possible to disable this feature.
Why is this an issue? Why ‘beware’? Most Linux distros ship with utilities like wget or curl which allow downloading arbitrary files from the Internet. Windows should have done this for ages, it is pretty annoying to resort to various hacks to download something from the Internet when working with the command line. Even though I do not think this is the main purpose of this app, at least there’s a less hacky but still hacky way to do it with built-in tools now. But why might this be a security threat? Is it auto elevated or does it shell execute the downloaded file automatically? If not, how is that dangerous? It is some app that has a syntax to download files off the Internet… Or is it because it is the “famed” Windows Defender?
The issue is because the tool is not intended to do that, then malicious actor can take advantage of it to download malicious tools without being noticed.
You know the OS has APIs for downloading files from the Internet anyway, any application can use them and the user is never notified, right? Okay, you may see, maintain an application whitelist. You know one can use PowerShell’s DownloadFile cmdlet or something similar, right? Okay, block script execution (I think, weirdly enough, it is off by default, thus its ‘great’ adoption) in PowerShell and PowerShell altogether maybe. You know one still has all the legacy scripting environments that allow file downloads, simply because it has always been like this, right? cscript is enabled by default in Windows, do what, delete that as well? It is pointless, the OS does not enforce a limitation on Internet connectivity for apps anyway, or execution of apps anyway, an attacker could easily copy an executable and use that to download whatever it may have. It’s a non-issue, Microsoft said the same recently.
curl.exe was added back in Windows 10 1803 and certutil.exe could already be used to download files before that.
Exactly.