There are seven new group policies in Windows 10 version 21H2 that Microsoft is about to add to Windows this fall. The Redmond software giant is expected to issue Windows 10 21H2 as a major feature update with a redesigned UI and new features.
Advertisеment
A few days ago Microsoft released Windows 10, version 21H1, and now the company is focused on the next update to the OS. Windows 10, version 21H1 is a minor update which shares its codebase with Windows 10, version 2004, and version 20H2, so all three releases receive patches from the same update branch. The only difference between them is an enablement package which turns on the appropriate features on top of the 2004 release.
Windows 10, version 21H2 is expected to be a different story. This release should bring drastic changes in the user interface, known as project Sun Valley, with design parts ported from now-cancelled Windows 10X. The Dev channel of the Windows Insider Program now gives us a preview of what may hit Windows 10 this fall, including a few new Group Policy options, as spotted by bleepingcomputer. To try them in action, open the Local Group Policy Editor app and navigate to the policy path, as specified below.
The new Local Group Policies in Windows 10 version 21H2
This policy can be found under Computer Configuration > Administrative Templates > Start Menu and Taskbar.
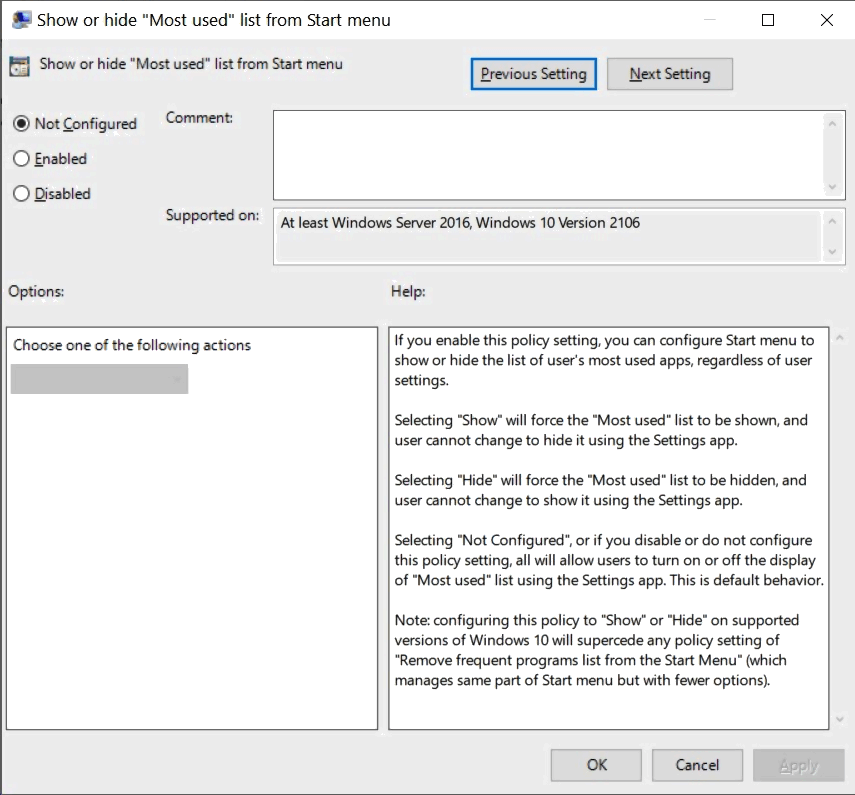
If you enable this policy setting, you can configure Start menu to show or hide the list of user's most used apps, regardless of user settings.
- Selecting "Show" will force the "Most used" list to be shown, and user cannot change to hide it using the Settings app.
- Selecting "Hide" will force the "Most used" list to be hidden, and user cannot change to show it using the Settings app.
- Selecting "Not Configured", or if you disable or do not configure this policy setting, all will allow users to turn on or off the display of "Most used" list using the Settings app. This is default behavior.
Note: configuring this policy to "Show" or "Hide" on supported versions of Windows 10 will supercede any policy setting of "Remove frequent programs list from the Start Menu" (which manages same part of Start menu but with fewer options).
Not allow sideloaded apps to auto-update in the background
This can be found at Computer Configuration > Administrative Templates > Windows Components > App Package Deployment. It manages a sideloaded apps' ability to auto-update in the background.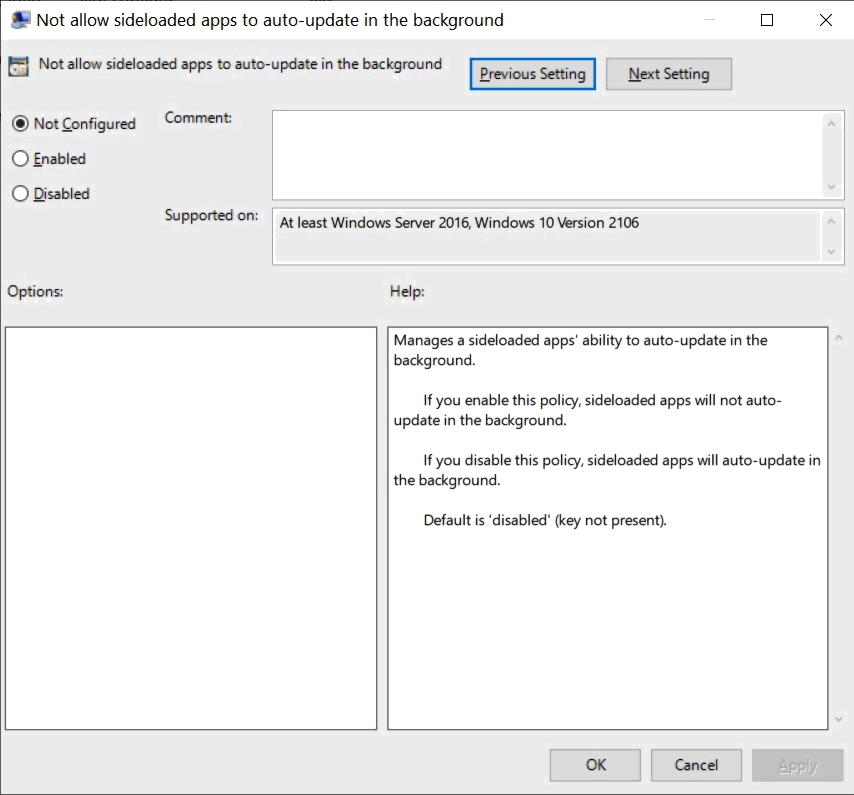
- If you enable this policy, sideloaded apps will not auto-update in the background.
- If you disable this policy, sideloaded apps will auto-update in the background.
- Default is 'disabled' (key not present).
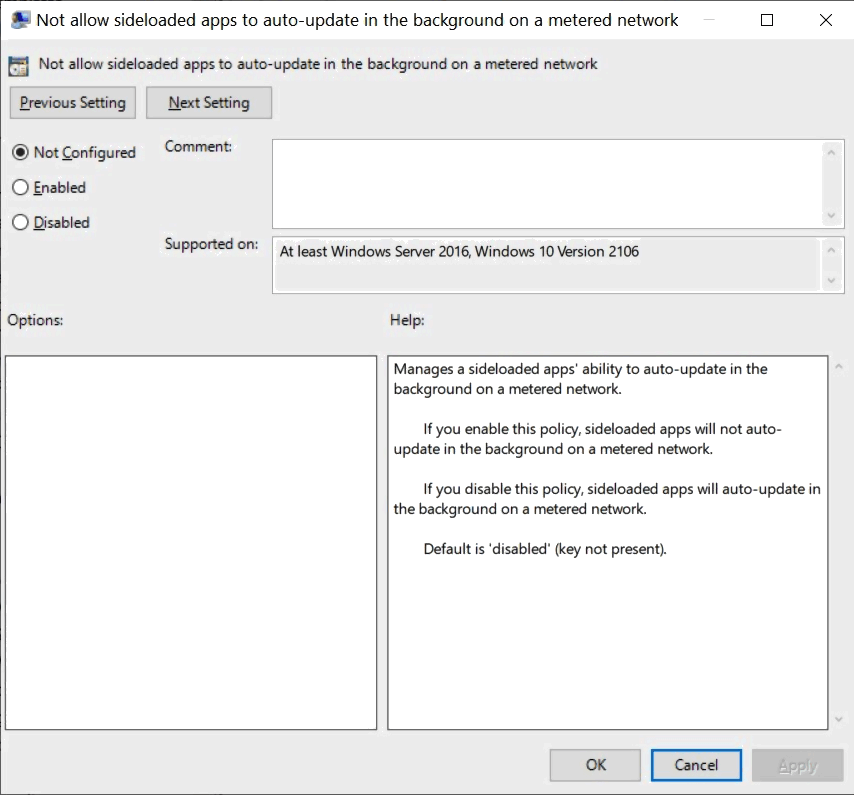
Not allow sideloaded apps to auto-update in the background on a metered network
Policy location: Computer Configuration > Administrative Templates > Windows Components > App Package Deployment
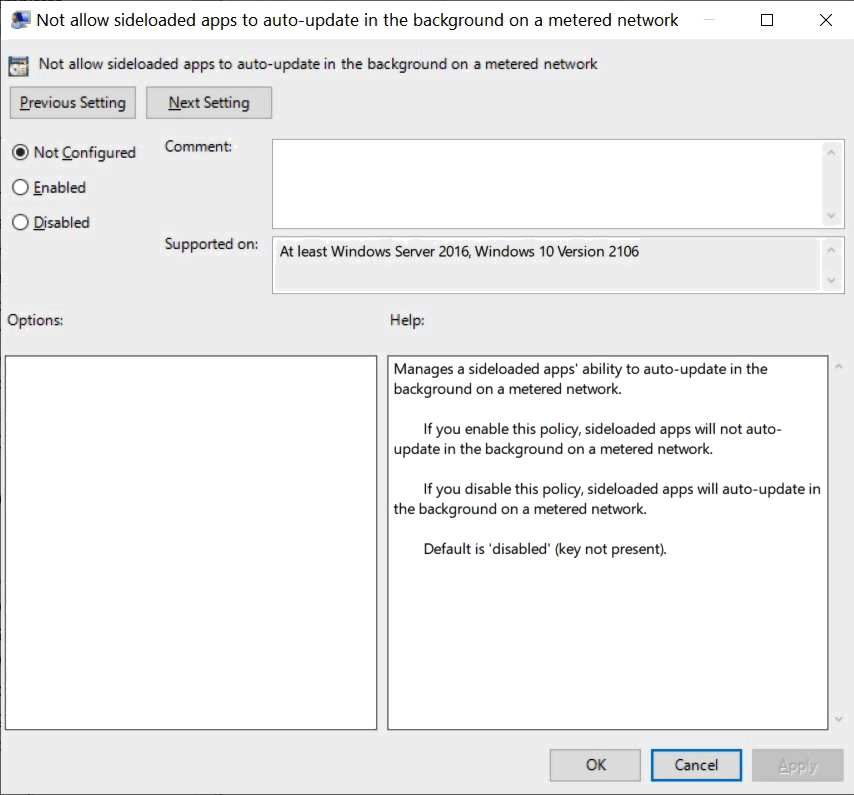
It manages a sideloaded apps' ability to auto-update in the background on a metered network.
- If you enable this policy, sideloaded apps will not auto-update in the background on a metered network.
- If you disable this policy, sideloaded apps will auto-update in the background on a metered network.
- Default is 'disabled' (key not present).
Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria
Can be found at Computer Configuration > Administrative Templates > System > Device Installation >Device Installation Restrictions
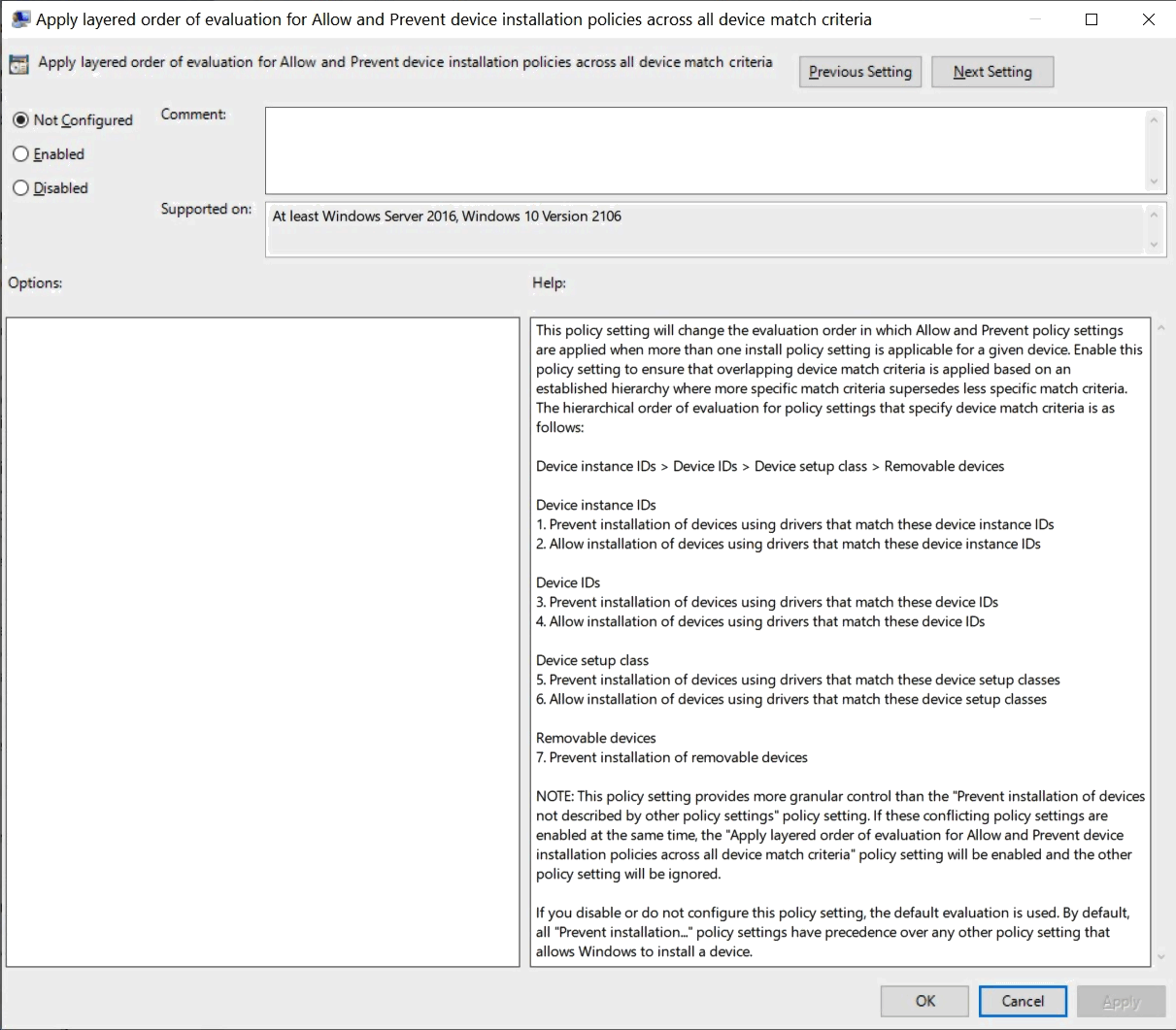
This policy setting will change the evaluation order in which Allow and Prevent policy settings are applied when more than one install policy setting is applicable for a given device. Enable this policy setting to ensure that overlapping device match criteria is applied based on an established hierarchy where more specific match criteria supersedes less specific match criteria. The hierarchical order of evaluation for policy settings that specify device match criteria is as follows:
Device instance IDs > Device IDs > Device setup class > Removable devices
- Device instance IDs
1. Prevent installation of devices using drivers that match these device instance IDs
2. Allow installation of devices using drivers that match these device instance IDs- Device IDs
3. Prevent installation of devices using drivers that match these device IDs
4. Allow installation of devices using drivers that match these device IDs- Device setup class
5. Prevent installation of devices using drivers that match these device setup classes
6. Allow installation of devices using drivers that match these device setup classes- Removable devices
7. Prevent installation of removable devices
- Removable devices
- Device setup class
- Device IDs
NOTE: This policy setting provides more granular control than the "Prevent installation of devices not described by other policy settings" policy setting. If these conflicting policy settings are enabled at the same time, the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting will be enabled and the other policy setting will be ignored.
If you disable or do not configure this policy setting, the default evaluation is used. By default, all "Prevent installation..." policy settings have precedence over any other policy setting that allows Windows to install a device.
Do not allow location redirection
This policy is located at Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection
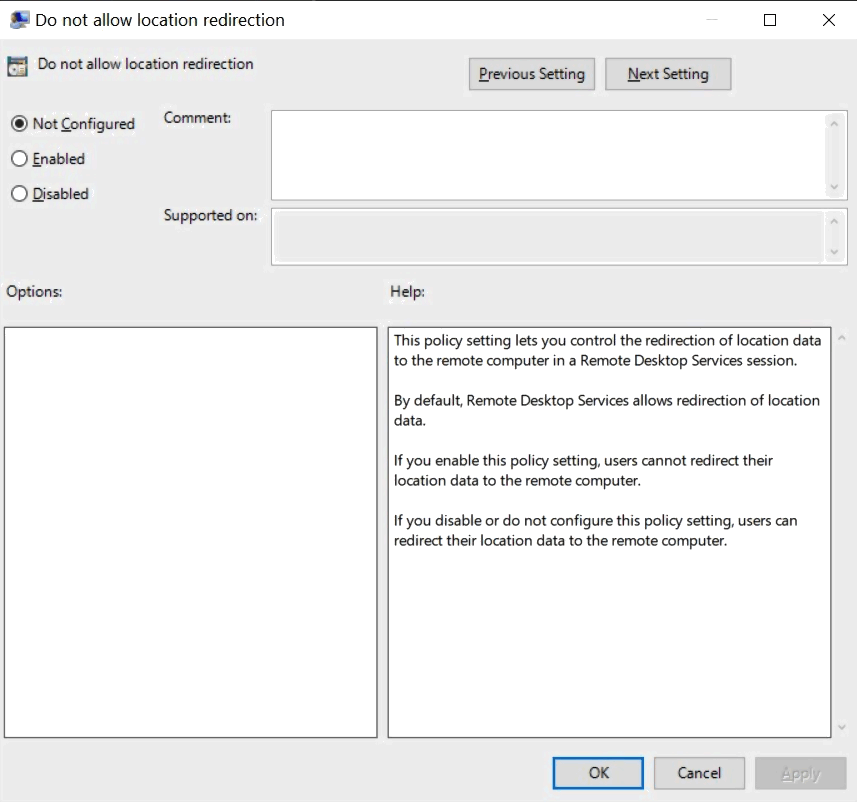
This policy setting lets you control the redirection of location data to the remote computer in a Remote Desktop Services session.
- By default, Remote Desktop Services allows redirection of location data.
- If you enable this policy setting, users cannot redirect their location data to the remote computer.
- If you disable or do not configure this policy setting, users can redirect their location data to the remote computer.
Allow UI Automation redirection
Policy location: Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection
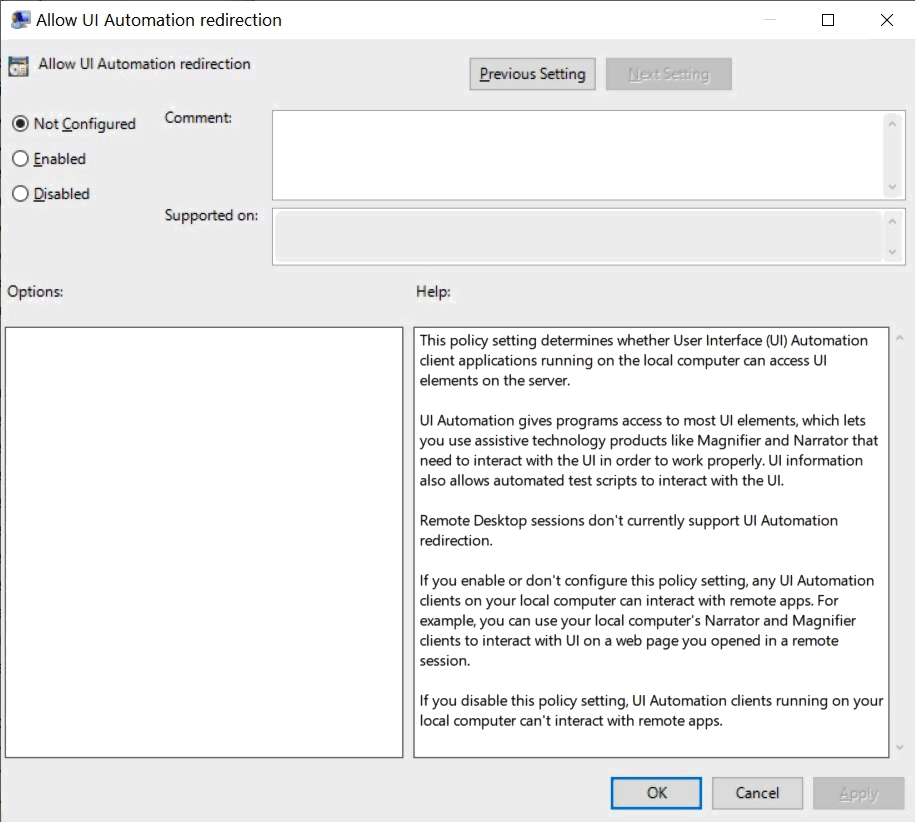
This policy setting determines whether User Interface (UI) Automation client applications running on the local computer can access UI elements on the server.
UI Automation gives programs access to most UI elements, which lets you use assistive technology products like Magnifier and Narrator that need to interact with the UI in order to work properly. UI information also allows automated test scripts to interact with the UI.
Remote Desktop sessions don't currently support UI Automation redirection.
- If you enable or don't configure this policy setting, any UI Automation clients on your local computer can interact with remote apps. For example, you can use your local computer's Narrator and Magnifier clients to interact with UI on a web page you opened in a remote session.
- If you disable this policy setting, UI Automation clients running on your local computer can't interact with remote apps.
Specify source service for specific classes of Windows Updates
Can be found at Computer Configuration > Administrative Templates > Windows Components > Windows Update
- When this policy is enabled, devices will receive Windows updates for the classes listed from the specified update source: either Windows Update or Windows Server Update Service.Note: To receive any updates from the Windows Server Update Service you must have properly configured an intranet Microsoft update service location via the “Specify intranet Microsoft update service location” policy.
- If this policy is not configured or is disabled, the device will continue to detect updates per your other policy configurations.Note: If you are using “Do not allow deferral policies to cause scans against Windows Update” currently to ensure devices only scan against your specified server, we recommend configuring this policy instead or in addition to such.
Found more? Don't hesitate to share your findings in the comments.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

I wish they had added a policy to control the folder shortcuts above the power button. That’s what’s been missing from the very beginning.
Who uses the Windows 10 Start? Use Open Shell for a better more customizable menu that also supports Group Policy and runs circles around Windows 10 Start.