This month, Microsoft fixed a vulnerability in Windows, identified as CVE-2025–21204 , that allowed attackers to perform and/or manipulate file management operations on a victim’s computer with the privileges of the NT AUTHORITY\SYSTEM account. To mitigate this issue, the April 2025 update introduced a new folder: %systemdrive%\inetpub , even for devices not running Internet Information Services (IIS).
However, this fix inadvertently introduced a new vulnerability that could prevent the installation of future Windows security updates, as highlighted by noted security researcher Kevin Beaumont.
The issue occurs because any user can create a symbolic link that redirects the system path C:\inetpub to another object, such as the Notepad application. Therefore, attempts to install the April 2025 update and likely future updates result in errors or rollbacks of changes made.
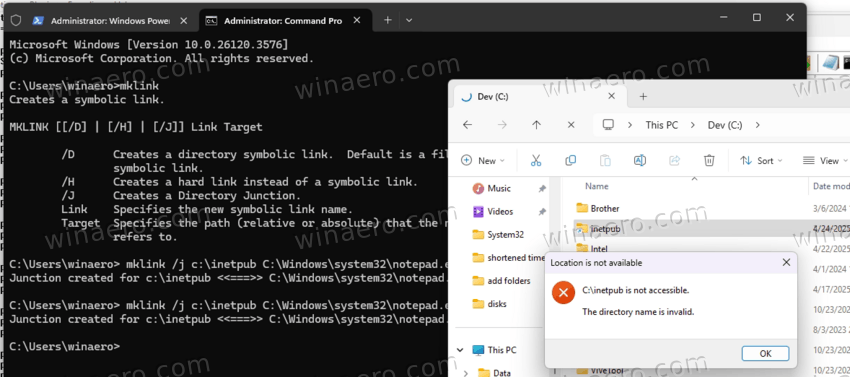
For example, the following command creates a symbolic link (in the screenshot above):
mklink /j c:\inetpub c:\windows\system32\notepad.exe
Malicious people can use this method to prevent the installation of future security updates that could fix vulnerabilities used to attack systems. However, running such a command requires administrator rights and physical access to the computer.
Beaumont reported the issue to the Microsoft Security Research Center (MSRC) about two weeks ago, but has not yet received a response.
Thanks to thecommunity.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Heh, similar to Unreal Engine 4 games – a patch fixes some bugs but (re)introduces other ones
From now on, every vulnerability should add a new strange folder to the root of the C: drive. That’s certainly the best way to make windows more secure!