Microsoft has announced a removal of the default Administrator account in Windows 11, which is being replaced with a new Administrator Protection feature. The new feature is designed to safeguard admin users while enabling them to perform essential tasks requiring elevated privileges.
Advertisеment
This new platform-level enhancement addresses vulnerabilities associated with running applications as an administrator, significantly reducing the risk of malware infiltration and lateral movement within systems. For IT professionals, developers, and everyday users, the change promises a more secure computing environment without sacrificing functionality.
How Administrator Protection Works
Applications operating with elevated privileges are often prime targets for cyberattacks. When malware gains access to these privileges, it can exploit systemwide changes, capture tokens, and compromise organizational security. According to the Microsoft Digital Defense Report 2024, token theft incidents have surged to approximately 39,000 per day, underscoring the urgent need for stronger safeguards.
Administrator Protection mitigates these risks by introducing several key design principles:
Just-in-Time Admin Tokens
Instead of granting persistent admin privileges, the feature generates temporary tokens only when needed. These tokens are created from a hidden, system-managed profile-separated local user account (SMAA) and discarded immediately after the task is completed.
Profile Separation
The SMAA operates independently of the primary user profile, ensuring that malicious code running in the unelevated context cannot compromise elevated processes. File systems and registry hives are no longer shared between elevated and unelevated modes, effectively neutralizing classic UAC bypass techniques like registry key manipulation or environment variable overloading.
Elimination of Auto-Elevation
Previously, certain Windows processes could automatically gain elevated privileges without user consent-a loophole exploited in UAC bypass attacks. With Administrator Protection, all auto-elevations have been removed, requiring explicit user authorization for every admin operation.
Windows Hello Integration
To enhance both security and convenience, Administrator Protection works seamlessly with Windows Hello, allowing users to authenticate via face recognition, fingerprint, or PIN during elevation prompts.
Key Design Highlights
Principle of Least Privilege
By enforcing stricter access controls, Administrator Protection ensures that admin users retain only the permissions necessary for specific tasks.
Non-Persistent Tokens
Elevated privileges exist only for the duration of the requesting process, minimizing exposure to potential threats.
Enhanced Security Boundary
The separation of profiles creates a robust barrier between user-level activities and elevated operations, preventing malware from accessing sensitive resources.
Behavioral Changes for Users and Developers
While Administrator Protection strengthens security, it also introduces notable behavioral shifts that users and developers must adapt to:
File and Registry Access
Files created in elevated mode are stored in the SMAA's library folders rather than the primary user’s directories. Similarly, the default registry hive maps to the SMAA’s registry instead of the primary user’s.
Application Settings Duplication
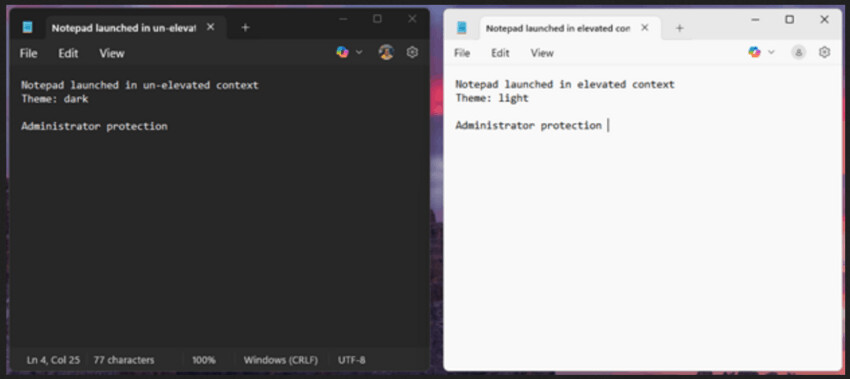
Customizations such as themes, fonts, or backgrounds applied in one context (elevated or unelevated) do not carry over to the other. For example, changing the theme in an unelevated instance of Notepad won’t reflect in its elevated counterpart.
Increased Elevation Prompts
With auto-elevation disabled, users may encounter more frequent prompts when performing admin tasks.
Recommendations for Application Developers
To ensure compatibility with Administrator Protection, developers should adhere to the following best practices:
- Avoid Installing Binaries Under User Profiles: Use %ProgramFiles% or %ProgramData% for installations, avoiding locations like %LOCALAPPDATA% or %USERPROFILE%.
- Minimize Elevation Needs: Design applications to run with least privilege, elevating only for specific tasks rather than upfront.
- Store Shared Files Appropriately: If files created in elevated mode need to be accessed unelevated, store them in the regular user’s directory to avoid cross-context complications.
- Eliminate Dependency on Auto-Elevation: Update applications to handle explicit elevation requests gracefully, improving both security and user experience.
General Guidelines for Users
- Always run applications non-elevated unless absolutely necessary.
- Be prepared to manage settings separately for elevated and unelevated contexts.
For example, when you change the theme to dark in the unelevated Notepad, the change will not be reflected automatically in the elevated Notepad. If you need parity you will need to make the change manually.
- Save files in standard library folders when working non-elevated to simplify retrieval later.
System Requirements and Availability
Administrator Protection is available starting with Windows 11 version 24H2 and later builds. It supports the following editions:
- Windows 11 Home
- Windows 11 Professional
- Windows 11 Enterprise
- Windows 11 Education
Preview builds are accessible through the Windows Insider Program, specifically in the Canary Channel (#27718+), with plans to roll out to the Dev Channel soon. However, the feature is not supported on:
- Windows Server editions
- Windows 365 Cloud PC
- Azure Virtual Desktop
- Windows 10 or legacy editions
If you don’t see the toggle to enable Administrator Protection under Account Protection in Windows Security Settings, ensure you’re using a supported build. Additionally, if Windows Hello isn’t prompting during elevation attempts:
- Reboot your device.
- Verify that Windows Hello is enabled.
Closing words
Administrator Protection represents a significant step forward in securing modern computing environments. By addressing long-standing vulnerabilities related to elevated privileges, Microsoft has enabled users and developers to work in a more secure and resilient ecosystem. As cyber threats continue to evolve, features like Administrator Protection underscore Microsoft’s commitment to delivering advanced security solutions tailored to today’s digital landscape.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

What are the implications of the change for things like sysprep?