Security researchers from Koi Security identified 11 malicious extensions within the official Chrome Web Store. These extensions include hidden features to monitor user activity, collect browser data, and redirect users to potentially harmful websites.
Advertisеment
The campaign, named RedDirection, primarily distributed extensions that appeared legitimate. Many of the extensions claimed to offer useful features such as color picking, virtual private network (VPN) services, volume boosting, and emoji keyboards. Despite offering the functionality they advertised, these extensions contained hidden tracking code.
Koi Security reported the findings to Google. However, some of the extensions remain accessible in the Chrome Web Store at the time of publication. Several extensions have verified developer profiles, hundreds of positive reviews, and appear prominently in Store search results, and look legitimate for the end user.
List of Identified Malicious Extensions
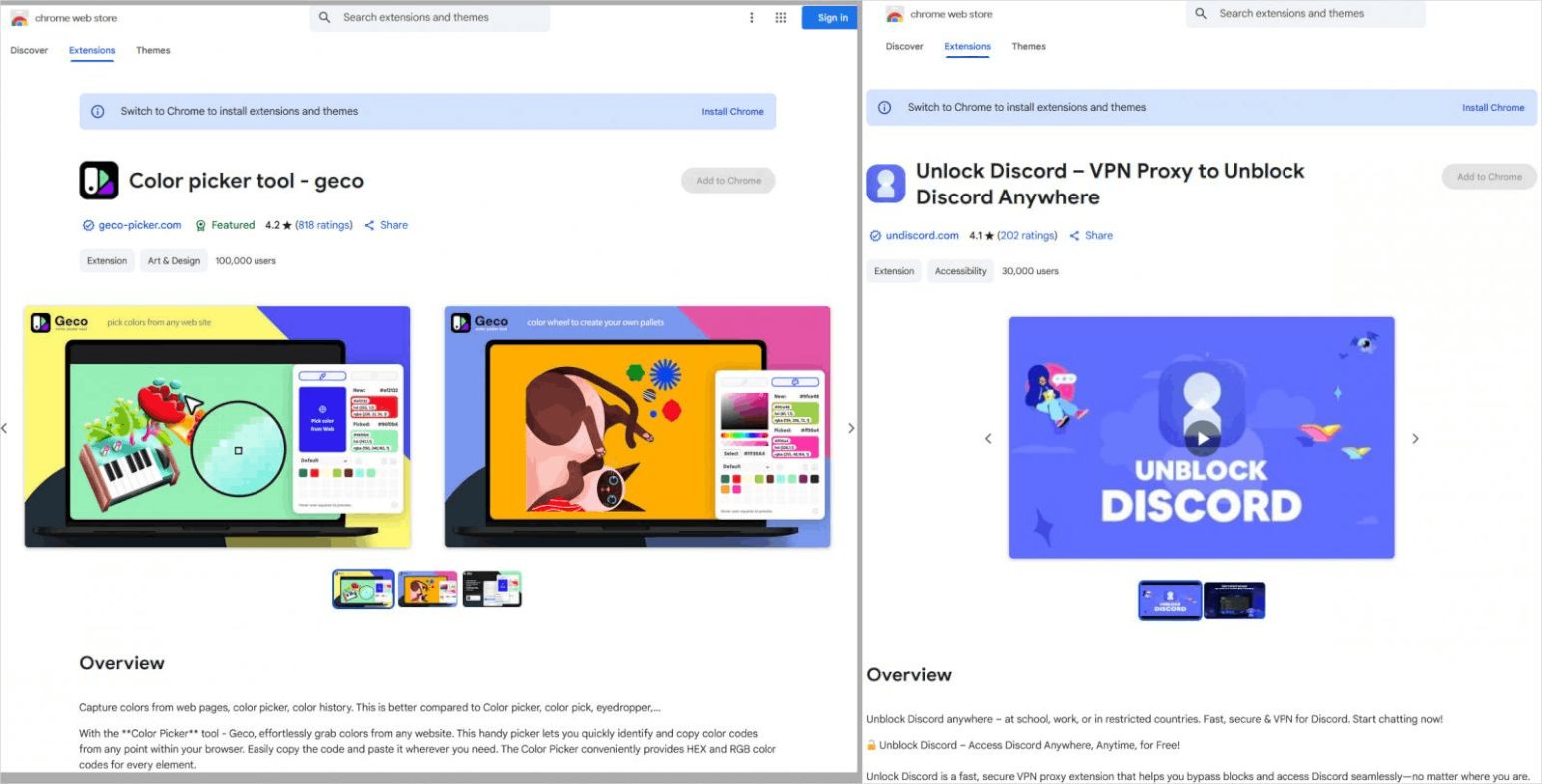
- Color Picker, Eyedropper – Geco colorpick
- Emoji keyboard online – copy&paste your emoji
- Free Weather Forecast
- Video Speed Controller – Video manager
- Unlock Discord – VPN Proxy to Unblock Discord Anywhere
- Dark Theme – Dark Reader for Chrome
- Volume Max – Ultimate Sound Booster
- Unblock TikTok – Seamless Access with One-Click Proxy
- Unlock YouTube VPN
- Unlock TikTok
The extension "Volume Max – Ultimate Sound Booster" previously drew attention last month from LayerX researchers, who suspected it of secretly collecting users' data, although conclusive evidence was not available at the time.
Technical Details of the Attack
Researchers discovered that the malicious code resides within a background service worker using the Chrome Extensions API. This component registers an event listener that activates whenever the user navigates to a new webpage. The listener captures the URL and transmits it to a remote server for user tracking.
The remote server may respond with a redirect URL, allowing attackers to manipulate browsing sessions and direct users to harmful websites. However, Koi Security did not observe active redirection during their testing phase.
Extension Compromise Timeline
Initial versions of these extensions did not contain malicious code. Developers introduced the harmful functionality later through updates. Some extensions remained tracking-free for several years. Quite possible they were obtained and modified by third parties who inserted the malicious components.
Microsoft Edge Extensions Also Affected
In addition to Chrome extensions, researchers found similar malicious extensions in the Microsoft Edge Addons store. These could affect over 600,000 users. The full list includes:
- Unlock TikTok
- Volume Booster – Increase your sound
- Web Sound Equalizer
- Header Value
- Flash Player – games emulator
- Youtube Unblocked
- SearchGPT – ChatGPT for Search Engine
- Unlock Discord
Impact
Combined, these 18 extensions across both browsers could infect more than 2.3 million users. Due to the automatic update mechanism in Chrome and Edge, users received the malicious versions silently and without explicit consent. Researchers describe this as one of the largest browser-based hacking campaigns observed to date.
Users are strongly advised to remove all listed extensions immediately. In addition, they should clear browser history, perform system-wide malware scans, and closely monitor their online accounts for any suspicious activity.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Luckily I don’t use any of these web extensions considered malicious in either Chromium-based browsers I using.