As you may already know, Windows Sandbox an isolated, temporary desktop environment where you can run untrusted software without the fear of lasting impact to your PC. In addition to the GUI method of enabling the feature, I would like to share two extra methods, PowerShell and DISM.
Advertisеment
Any software installed in Windows Sandbox stays only in the sandbox and cannot affect your host. Once Windows Sandbox is closed, all the software with all its files and state are permanently deleted.
Windows Sandbox has the following properties:
- Part of Windows – everything required for this feature ships with Windows 10 Pro and Enterprise. No need to download a VHD!
- Pristine – every time Windows Sandbox runs, it’s as clean as a brand-new installation of Windows
- Disposable – nothing persists on the device; everything is discarded after you close the application
- Secure – uses hardware-based virtualization for kernel isolation, which relies on the Microsoft’s hypervisor to run a separate kernel which isolates Windows Sandbox from the host
- Efficient – uses integrated kernel scheduler, smart memory management, and virtual GPU
Windows Sandbox has the following pre-requisites.
- Windows 10 Pro or Enterprise build 18305 or later
- AMD64 architecture
- Virtualization capabilities enabled in BIOS
- At least 4GB of RAM (8GB recommended)
- At least 1 GB of free disk space (SSD recommended)
- At least 2 CPU cores (4 cores with hyperthreading recommended)
Also, there is an unofficial way to enable Sandbox in Windows 10 Home.
As you may already know, it is possible to turn on or off Windows 10 Sandbox in Optional Windows Features.
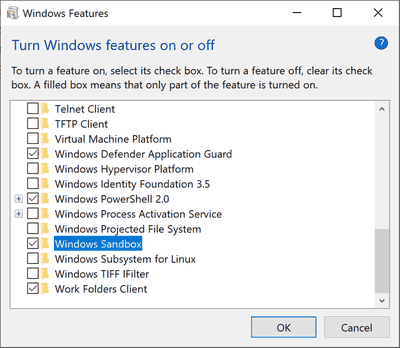
Alternatively, this can be done with PowerShell, and DISM.
Note: Before proceeding, you need to enable virtualization, as follows.
- If you are using a physical machine, ensure virtualization capabilities are enabled in the BIOS.
- If you are using a virtual machine, enable nested virtualization with this PowerShell cmdlet:
- Set-VMProcessor -VMName <VMName> -ExposeVirtualizationExtensions $true
To Enable Windows 10 Sandbox with PowerShell,
- Open PowerShell as Administrator.Tip: You can add "Open PowerShell As Administrator" context menu.
- Type or copy-paste the following command:
Enable-WindowsOptionalFeature -FeatureName "Containers-DisposableClientVM" -All -Online
- When prompted to restart the computer, type Y, and press Enter.
- The change can be undone with the following command:
Disable-WindowsOptionalFeature -FeatureName "Containers-DisposableClientVM" -Online
You are done.
The console DISM tool can also be used to enable or disable Windows 10 Sandbox. Here's how.
Enable Windows 10 Sandbox with DISM
- Open an elevated command prompt.
- Type or copy-paste the following command:
dism /online /Enable-Feature /FeatureName:"Containers-DisposableClientVM" -All
- Restart the computer when prompted.
- To disable the Sandbox feature, use this command:
dism /online /Disable-Feature /FeatureName:"Containers-DisposableClientVM"
That's it.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Thanks this works for mounted image also — dism /image: /Enable-Feature /FeatureName:”Containers-DisposableClientVM” -All
dism /image:pathtomountfolder /Enable-Feature /FeatureName:”Containers-DisposableClientVM” -All