Google Chrome 127 is available in the stable channel. The release it focused on security. It improves the Ingonito mode by enabling HTTPS-First by default. Google is also starts killing Manifest V2 in flavor of Manifest V3, with the latter being not friendly to ad blockers. Finally, there are some changes to Safe Browsing. First of all, the browser will now ask a password for encrypted archives. If you specify it, Chrome will send the contents to Google to check the files for safety. Also, Enhanced protection now includes extra telemetry that checks some pages against a block list.
Advertisеment
What's new in Chrome 127
Incognito mode
Incognito mode now comes with the "HTTPS-First" enabled by default, which automatically redirects HTTP requests to HTTPS. To ensure work with sites that do not support HTTPS, it has a fallback to HTTP if the request cannot be completed via HTTPS (e.g. due to certificate issues). When trying to open a site via HTTP, it shows a special warning.
Safe Browsing Improvements
Turning on enhanced browser protection (Safe Browsing > Enhanced protection) sends extra data to Google about the pages you visit that use APIs for vibration or full mouse and keyboard control. If a page is on the block list, you'll see a warning, and these marked APIs won't work.
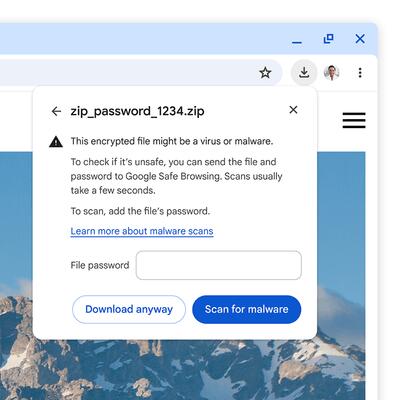
Download handling
The enhanced protection mode in the browser (Safe Browsing > Enhanced protection) now summarizes improvements in scanning downloaded files. It allows sending executable files and suspicious archives to Google for virus and malware checks. When downloading encrypted archives (.zip, .7z, .rar), the browser prompts for a password to decrypt for scanning. Users can decline or provide the password, which then sends the archive with its password to Google for scanning. In the standard Safe Browsing mode, a password prompt appears too, but only the metadata and hashes are sent to Google, not the archive contents.
Auto Full Screen mode
The new "Automatic Fullscreen" option (found at chrome://settings/content/automaticFullScreen) has been introduced, letting sites enter full-screen mode via the Element.requestFullscreen() method without needing user approval. It also keeps browser prompts visible in full-screen. By default, this feature is off but can be activated for specific sites and apps. When used with the Window Management API and pop-up settings (chrome://settings/content/popups), it simplifies operations like launching full-screen pop-ups on a second monitor, displaying content across multiple screens, or moving full-screen views between displays.
Certificate Root Store
Chrome's built-in Root Store will no longer trust Entrust certificates. This is because of several rule breaches, like not meeting response times for certificate issues, delays in revoking certificates, incorrect incident reporting, and not following EV TLS certificate issuance rules which check domain ownership. Chrome will mark Entrust's TLS certificates issued after October 31, 2024, as untrusted. Certificates from before this date will remain trusted.
Manifest V2 deprecation
Chrome 127 has started Manifest V2 disablement. The manifest defines what add-ons can use from the WebExtensions API. Currently, only some Chrome test builds are disabling add-ons using Manifest V2. The complete switch to Manifest V3 is expected by June 2025. Manifest V3 is being criticized for removing major APIs that needed by ad-blockers. It is worth noting that major add-ons already have versions compatible with the new Manifest version.
Other changes
- A preliminary version of the Private Network Access specification has been introduced. It restricts downloading resources from public websites that link to hosts within a private network (like 127.0.0.0/8, 192.168.0.0/16, 10.0.0.0/8). Currently, these downloads are only permitted when a page is visited via a secure connection (HTTPS). Plans are in place to eventually tighten controls to prevent unrestricted access to internal intranet subnets from public sites. This move aims to thwart attacks like CSRF, which target internal devices such as routers, access points, printers, and corporate web interfaces that only take local network requests.
- During "Origin trials," there's an experimental feature to block access to IP 0.0.0.0. This is because on Linux and macOS systems, this IP can be exploited to circumvent the block on IP 127.0.0.1, which is localhost.
Chrome for Android
- The Android version features a streamlined process for connecting to a Google account and syncing data like passwords and bookmarks. Sync is now part of the account sign-in experience and isn't a separate setting anymore.
- The Android version features an updated password management interface. Users who are connected to their Google account but have not enabled synchronization are now able to save and use passwords linked to their Google account.
The latest release also addresses 24 security issues. These were largely detected through automated tools like AddressSanitizer, MemorySanitizer, Control Flow Integrity, LibFuzzer, and AFL. Five of the vulnerabilities are marked as high risk, though none are critical enough to override all browser safeguards and run code outside the sandbox. Google's vulnerability reward program has paid out 16 bounties for this release, totaling $47.5 thousand, with individual rewards ranging from $500 to $11,000. The value of six bounties is still pending.
Existing browser users will receive it automatically. Others can download it manually from the official website.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
