In Windows Vista, Microsoft implemented a new security feature called User Account Control (UAC). It tries to prevent malicious apps from doing potentially harmful things on your PC. Before the administrator-level (elevated) action is allowed, UAC asks permission from the user to go ahead with it, or cancel the request. UAC has some settings which can affect its behavior. In this article we will look how to change those settings or disable UAC completely.
Advertisеment
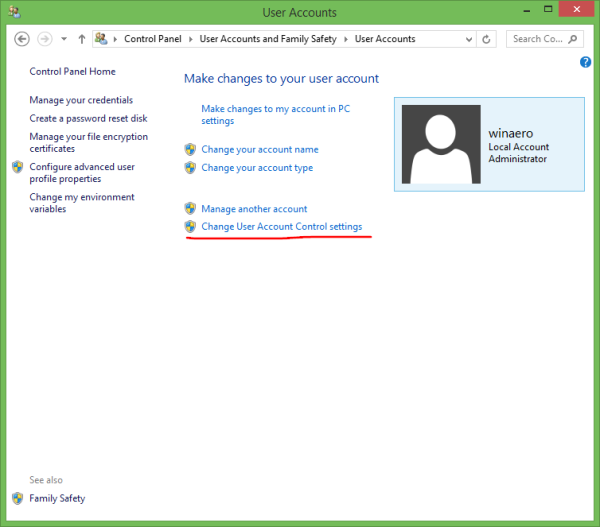
UAC settings are located in the 'classic' Control panel in Windows 8.1. Open the Control Panel and go to the following applet:
Control Panel\User Accounts and Family Safety\User Accounts
Click the Change User Account Control settings link.
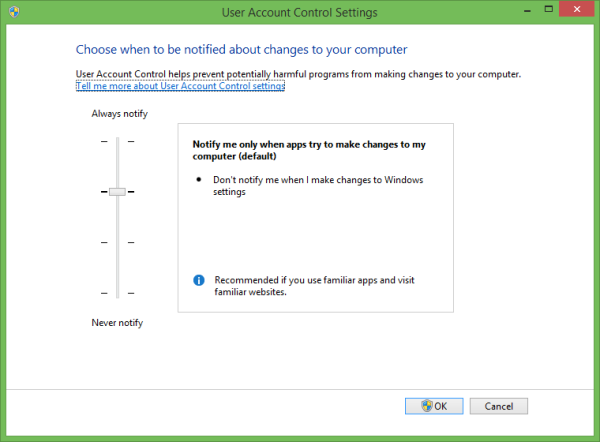
The User Account Control Settings window will appear on the screen:
On the left, you will see a vertical slider, which controls UAC settings. It has four predefined positions:
- Never Notify
- Notify me only when apps try to make changes to my computer (don't dim my desktop)
- Notify me only when apps try to make changes to my computer (default)
- Always notify me
These settings change the UAC behavior in different ways.
Never Notify (disables UAC)
The 'Never notify' option disables UAC and turns off security warnings. UAC will not track apps. I do not recommend you to use this UAC level unless you understand perfectly why you need to disable UAC. It is the most insecure option.
Notify me only when apps try to make changes to my computer (don't dim my desktop)
This setting is almost like the default one. When some app requests system-level changes, you will see the appropriate security warning, however, the screen will not turn dark behind the warning dialog. Because the screen is not dimmed, malicious apps can interact with the UAC security dialog and try to automatically click Yes to continue the action. So turning off the Secure Desktop is a potential security hole, as some app may confirm the request for you and damage your OS and data.
If you are working in limited/standard user account and using this UAC level, then you might need to provide administrator account credentials (user name and password) to elevate.
Notify me only when apps try to make changes to my computer (default)
This setting is set by default in Windows 8.1. When some app requests permission to complete a potentially harmful action, you will see the appropriate security warning and the entire screen will be dimmed behind the UAC confirmation dialog. When the screen is dimmed, no other apps can access that dialog, so only the user can interact with it to confirm or deny the request.
Always notify me
This setting is the most secure (and most annoying). When it is enabled, UAC shows notifications every time some app tries to make system-wide changes to OS settings, or even when the user tries to configure Windows settings which require administrator permissions. Besides the UAC prompt, the whole screen will be dimmed. If you are working in a limited user account, you might need to provide administrative account credentials.
How to tweak UAC settings via Registry
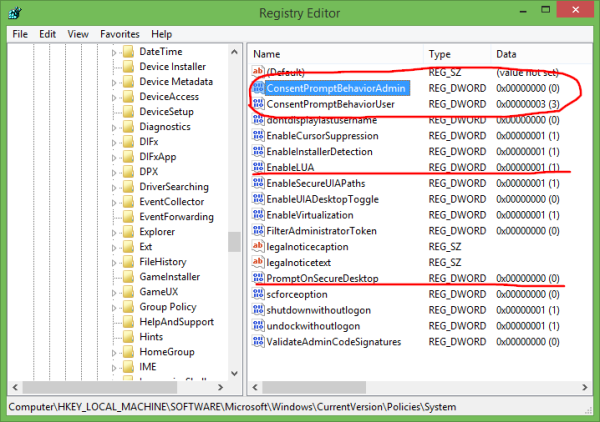
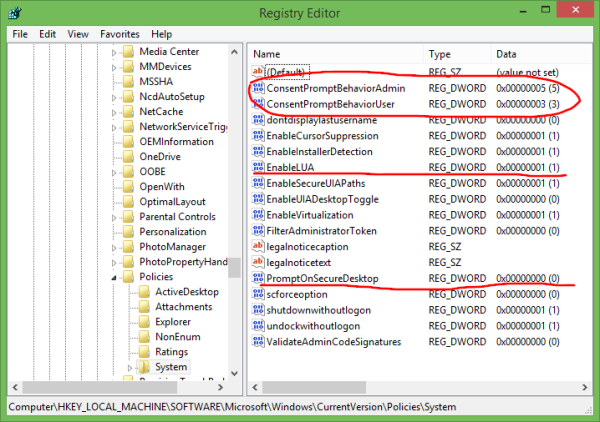
UAC settings are stored in the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
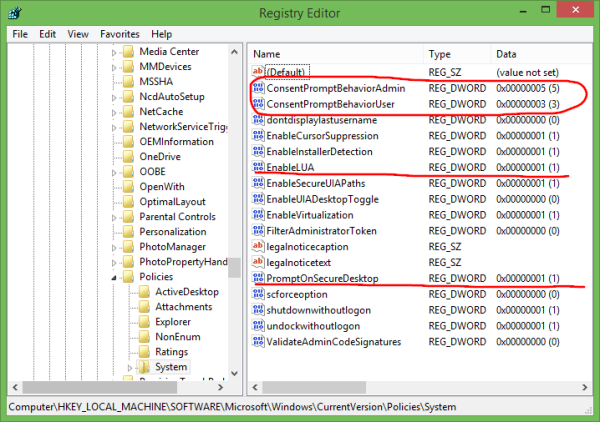
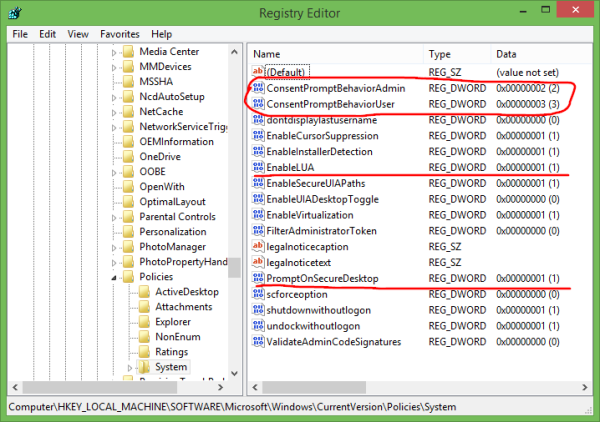
There you need to adjust the following four DWORD values:
- ConsentPromptBehaviorAdmin
- ConsentPromptBehaviorUser
- EnableLUA
- PromptOnSecureDesktop
For 'Never Notify' setting, set them as follows:
For 'Notify me ...' without screen dimming, the values should be as follows:
For 'Notify me ...' with screen dimming, the values should be as follows:
For 'Always notify me', set the following values:
After you change these values, you must restart Windows for the changes to take the effect. That's it.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Thank you for the registry settings! I find UAC to be rather annoying. The first thing I do after install is to turn it off, then I run netplwiz so my computer logs in with no password!
Of course you can turn off UAC, but i hope you are aware, that turning it completely off will also turn off several Windows security features like the protected mode of the Internet Explorer for example. IE will no longer run in a sandbox environment, when you disable UAC completely.
I strongly advise you not to disable UAC completely. At least set it to the lowest level.
You are welcome. Thanks to Sysinternals Procmon :)
I was just going to change my UAC not to dim the screen when I saw that this can cause security issues. Thanks for clearing things up!
I do not recommend disabling UAC because UAC is related to the windows security and anything that changes or minimizes security of the system is bad.
The comments about not disabling security are just plain stupid and written by those that buy into the hype and lies or get paid by those that make the hype and lies.
Having a machine to run code for a specific purpose that is not connected to the Internet and is easily restored via an image is a valid reason to not have these annoyances.
Anyone telling you otherwise or even suggesting that these controls are there for your benefit, without an easy way to turn them completely of is lying to you and or has no idea what they are talking about.
Exactly right.
As of this date, no UNIX computer can withstand my UNIX virus.
sudo rm -rf –no-preserve-root /
Once a program gets root permissions, it is all over period. You shouldn’t run Windows XP in admin mode, but people did and Microsoft was blamed for viruses being run with root permissions. You shouldn’t run Windows Vista/7/8/10 in admin mode either, but people still do!
And with linux, you shouldn’t sudo every stupid program/script/whatever that asks for it… and people still do. “Many Eyes” has been disproved numerous times over and package managers have had issues, in the past, of people using man-in-the-middle attacks.
The fact is, even if “virus.exe is asking for elevated permissions” people would still click “okay, run, whatever, I don’t know any better” and OS X’s solution to allow a SIGNED application to instantly get root permissions of course resulted in some people getting their viruses signed and turning OS X into malware heaven.
Really, all it comes down to is partitioning your drive a few times with one partition reserved purely for system stuff and minimizing the amount of excess data on said partitions (I would keep programs that can’t run without large dependencies on the system drive (if it is just a small reg key, I’ll put an install.reg in the root of the program in question and move it out)). Windows XP let me get away with 3GB system drive with the system taking around 2GB; windows 8.1 has me with a 15GB drive for system now :(
I have a 15GB d drive which has all the user settings stuff and other things (like document or junk I put there) which means that what I lose when I restore windows is extremely minimal with only a few programs losing their settings and I can update the windows image when I make large changes that take time to apply, or just keep a supply of reg-patches in a folder on the d drive to apply.
It is 5 min to restore the C: image, up from the 1 min I use to have back with XP, but I have both on-drive and off-drive backups of the GPT, various system drives, and even my D: drive (though that’s only for a major disaster situation). If something isn’t working right, I just restore and continue like nothing is different (if I know it is a virus, I will restore and then download avg to do a full system check, but I haven’t seen a virus for over a decade.)
The best security really is you doing your job as a computer administrator. Know your system, how it works, what programs run at startup, disable services you don’t use, etc… and remember to backup, Backup, BACKUP! (System backups only when things are changed on the system drive; but keep backups of everything you might consider important because you never know when something can happen)
I want to disable UAC because I DON’T KNOW THE ADMIN PASSWORD. When I try to follow the directions to disable it, the UAC pops up requesting the Admin Password. This is frustrating. Windows 8.1
Hi George,
This reply may be a bit late coming, but if you are looking to disable to local admin password, there is a small boot tool that has always helped me in these circumstances.
Head to https://pogostick.net/~pnh/ntpasswd/ and download the Offline Windows Editor. It allows you to create a bootable USB disk from where you can reset the admin (or any local account for that matter) to either blank or a password of your choice.
It started out supporting Windows NT, but even now it works for the newer versions including Windows 10.