As you may know, Windows Vista introduced some major changes to the security model of Windows, including User Account Control. What UAC does is introduce the concept of apps having the least privilege - only enough permissions that apps need to run should be granted to them and not full admin permissions, because if malware or bad apps run as admin, they can pretty much do any damage to your OS.
However, thanks to UAC, the user experience gets spoiled slightly and decades-old Windows users who were not used to this concept or who were not explained why it was introduced were bewildered when they migrated from Windows XP. They didn't understand why they were asked to confirm any action that does system level changes to their PC. One such application that shows considerable amount of UAC prompts if you are running Windows with the highest level of the UAC setting is File Explorer (formerly known as Windows Explorer). While Explorer does not show that many UAC prompts at the default UAC setting, the default UAC setting is not 100% foolproof. It is only secure against apps that assume admin level privileges to do bad things.
Advertisеment
Now you might ask why would you want to run Explorer as administrator in the first place? Suppose you need to do some file operations that involve lots of UAC prompts. Or maybe some shell extension (e.g. right click menu extension) still hasn't been updated to work with UAC and it fails to work until it is run as admin. There is no Microsoft-provided way to elevate shell extensions that fail to work properly. So rather than always running all apps with UAC set to the default setting, you could set UAC to the highest level permanently and instead temporarily elevate the File Explorer in a separate process so you could get your stuff done as admin and then close it.
Except the problem is that Microsoft does not allow running Explorer as administrator in Windows 8.1/8 (and in Windows 7 too). In Windows Vista it was possible to run Explorer as administrator. Microsoft uses DCOM to launch Explorer in Windows 7 and later versions. A DCOM class factory checks if the user is running interactively and launches Explorer. They put in a restriction in the registry as a security measure to prevent running it as administrator. Of course, if you are using a third party file manager to do file operations, then it's no problem as you can easily elevate it temporarily.
In this article, we will see how to elevate Explorer so you can do your file operations which show too many UAC prompts or use shell extensions that don't work without elevating. We will also see how to close the elevated process. The solution to run Explorer elevated was found by one of our readers and Windows enthusiast, Andre Ziegler, who pointed the reg key used by the DCOM class in this Technet Forums thread. Here is how you can do it:
1. Download and open Winaero's excellent RegOwnershipEx application. RegOwnership allows you to take ownership of registry keys and grant admin permissions and later restore them, all from an easy-to-use user interface.
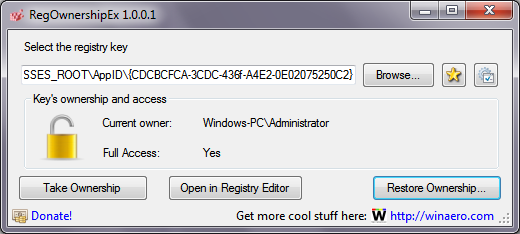
2. In the 'Select the Registry Key' text box of RegOwnershipEx, copy and paste the following:
HKEY_CLASSES_ROOT\AppID\{CDCBCFCA-3CDC-436f-A4E2-0E02075250C2}3. Click the Take Ownership button. You will see the Lock icon getting unlocked. Now click 'Open in Registry Editor'.
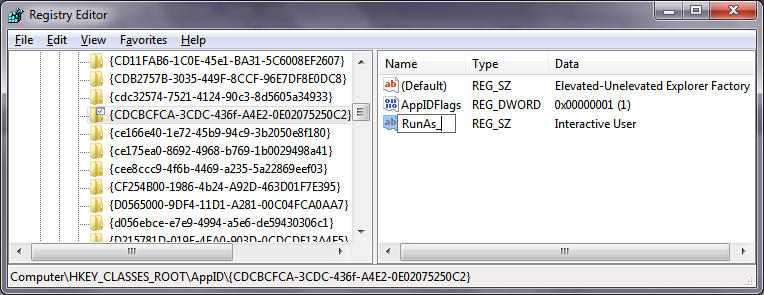
4. Registry Editor will open at the above key. In the right pane of Registry Editor, you will see a value named 'RunAs'. You need to simply rename this value or delete it so Windows allows you to run Explorer as administrator when you need it. Rename 'RunAs' to anything. For example, RunAsAdmin (so you remember you made this change).
5. Close Registry Editor and now switch back to RegOwnershipEx. Click the 'Restore Ownership' button, tick the key that you just took ownership of and restore its ownership.
That's it. Now if you right click Explorer.exe or a shortcut to it and select 'Run as administrator', you will be able to run it as admin! Another way to run it as admin is to start the Computer/This PC shortcut from the Start Menu or Start screen by pressing Ctrl+Shift+Enter. It will start as a separate process which you can see in Task Manager or SysInternals' excellent Process Explorer.
You can also use Winaero's simple but useful ELE.exe app to start any program as administrator from the command line.
When you run it as administrator, no matter what you do inside it, you won't be shown a UAC prompt. If you run Process Explorer as administrator too, it will show the integrity level of the second Explorer process as High (High means that the process is running as administrator).
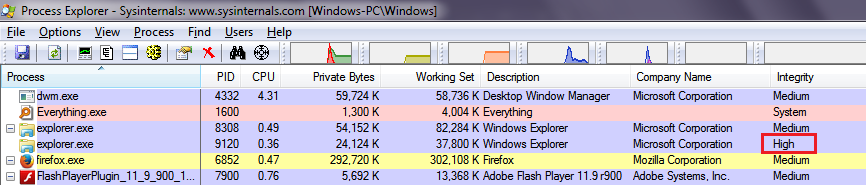
Now the important thing to note is that this process does not cleanly exit when you close the Explorer window! You must remember to terminate it every time you elevate Explorer after you are done working in the Explorer window.
Also, you should not run Explorer as administrator on a regular basis. You should only elevate it if you need to use some incompatible shell extension or if you need to do multiple heavy-duty file operations which are going to produce lots of annoying UAC prompts to manage and maintain files and folders on your hard drive. And remember to end the second Explorer.exe process in Task Manager after you are finished working with it.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:

Very Nice!
Thank you very much for kind words.
It doesn’t work!
Of course it does. You must be doing one of the steps incorrectly.
This article has been exceptionally useful! I have been searching for this information for some time.
At my workplace, when users see a password prompt they tend to ask me for the password and are always pushy about it or take it personally when i tell them no, so i set the machines UAC policy to auto deny elevate (so it will throw an error instead of asking a password).
This changed the conversation from ‘Can i have the password for just a second please? Why not? Don’t you trust me? I’m not going to tell anyone!’ to ‘Excuse me, my computer is giving me an error can you fix it please?’ The downside has always been switching users for certain tasks since runas /user:xyz cannot run explorer under new permissions.
Today sir, you have made my day and i owe you a beer :)
It’s our pleasure to be of help
I`m actually going to set my computer on fire becasue of the idiots who made this heap of garbage. It`s when you reach then point when something on your computer tells you you have to run explorer as admin and you find out they have made it damn near impossible for a normal human being to run explorer as admin in windows 8.1, that`s when I say [censored] this and [censored] the people who made it, burn baby burn. It`s so stupid, it`s such a simple little detail, run explorer as admin but they had to [censored] it up. They had to make it difficult. I`m done with computers and I hate everyone who makes them and the software too. Every [censored]ing time I try to get something done, I run into the brainfart of some idiot somewhere and I cant take it anymore.
Looks like this made you mad :)
This is a lovely idea, but I couldn’t get it to work on Windows 8.1.
RegOwnershipEx works exactly as described.
But renaming or deleting the RunAs key didn’t make any difference as far as I could see. In Process Explorer there was no explorer.exe with Integrity High. And the double right-click context menu of File Explorer pinned to the task bar does not show the Run as administrator option. (The menu shows the same 2 options, “Open” and “Properties” with or without the RunAs key.)
I wondered if a reboot was needed for the new reg setting to take effect but it didn’t make a difference.
Looking at the properties of the pinned File Explorer, on the Shortcut tab, the Target is “File Explorer”. What is this target? Can someone explain how this finds its way to the .exe file?
On a whim, I tried making a new shortcut with the Target “C:\Windows\explorer.exe” and pinning it to the task bar. When I right click twice, the 4 options are “Open”, “Run as administrator”, “Unpin from Taskbar”, and “Properties”. So here’s a simple way to run File Explorer as administrator. No need for a utility program and changing the registry. Admittedly, it does require knowing to look for explorer.exe and where to find it.
Am I missing something here?
I think your way does work – so far no UAC popups. if you look at the normal explorer pinned taskbar icon overlay says ‘File Explorer’, but the pinned ‘C:/windows/explorer.exe’ says ‘Windows Explorer’ – thanks.
You can even change the shortcut properties to auto run as administrator.
Correction – if Bill’s approach was to resolve “You don’t currently have permission to access this folder” prompts as well than it’s not working.
Umm why exactly is any of these edits needed? I’ve never had problems with simply opening a command prompt with admin privilliages and executing explorer.exe from there (it gets executed with admin rights if cmd.exe has admin rights)
Oh and incase someone would need the whole explorer.exe process to have admin right not just a single windows then wouldn’t taskkill /IM explorer.exe /F&start explorer.exe be sufficient from an elevated prompt to have the whole process start with admin rights?