Microsoft has unveiled the open source Hyperlight hypervisor project. The solution is designed to be embedded into applications for isolated execution of code that is untrusted or requires special protection. The project's source code is written in Rust and published on GitHub under the Apache 2.0 license.
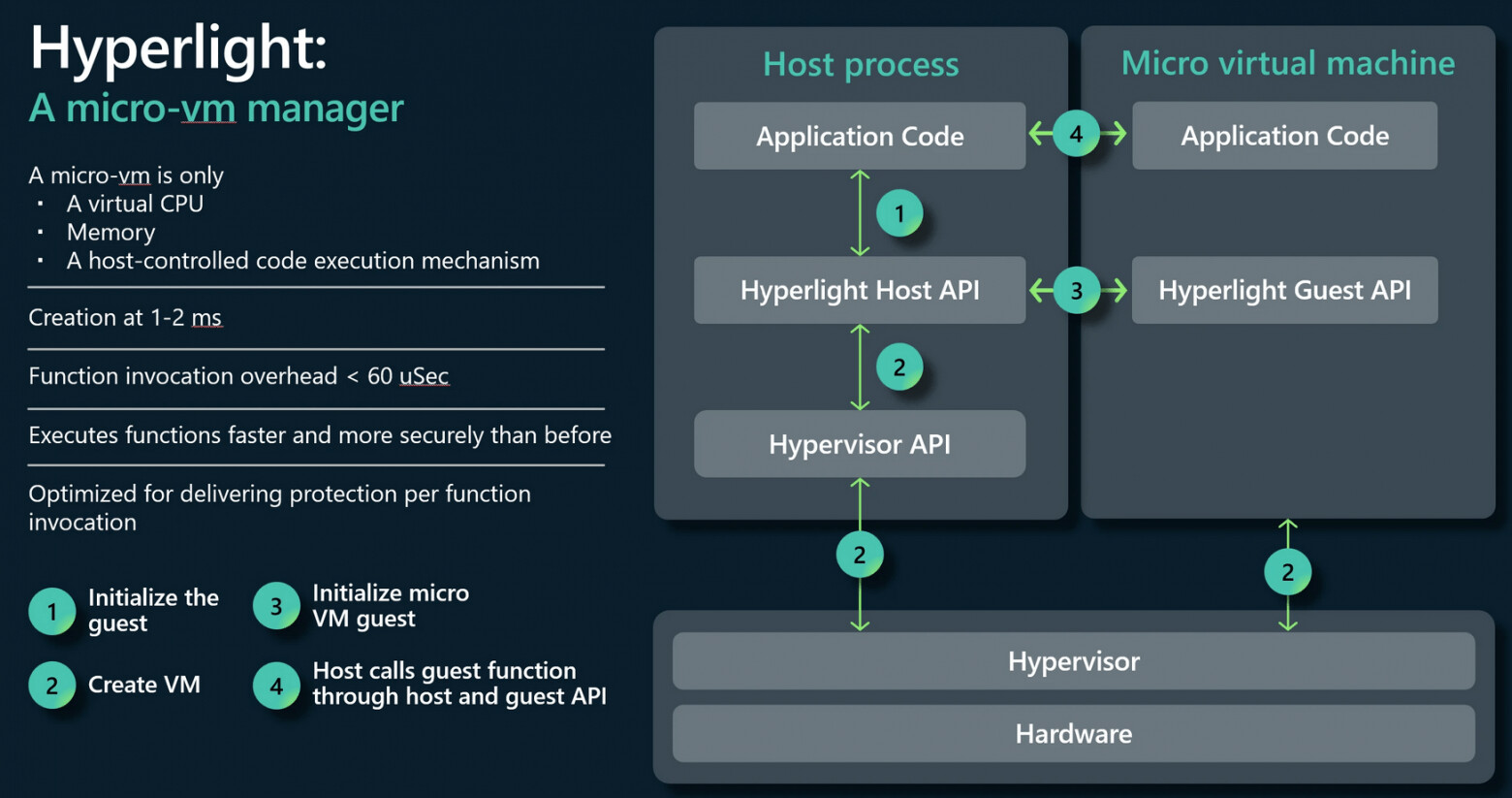
The hypervisor is a shared library that enables the execution of individual functions in lightweight virtual machines (micro-VM) and organizes data exchange with these functions.
Hyperlight achieves low latency and minimal overhead compared to traditional VM launches. The hypervisor has 1-2 millisecond latency to create VMs, allowing for isolation at the function launch level. In comparison, a regular VM launches in no less than 120 milliseconds, and an isolated sandbox environment for WebAssembly code execution using the Wasmtime runtime takes 0.03 milliseconds to launch.
For isolation on the Linux platform, it supports KVM and mshv (Microsoft Hypervisor in Azure Linux) hypervisors. On the Windows platform it can use WHP (Windows Hypervisor Platform) and WSL2 (Windows Subsystem for Linux 2) with KVM. The macOS platform is not supported yet.
It doesn't provide a separate kernel and operating system for a virtual machine. Virtual machines are more like a self-sufficient bootable program that includes the code of the launched software in the binding of runtime and a specialized minimal kernel. The VM is using a single linear fragment of memory and a virtual CPU, without device mapping and without division into processes.
The development process is based on linking the main application code with the Hyperlight Host library, which coordinates the launch of virtual machines, as well as the code of functions launched in isolated mode (guest functions) with the Hyperlight Guest library. The latter provides an API for interacting with the external part of the application and the ability to run code separately without an operating system environment.
The provided layer for interaction between the host application and isolated functions allows not only to call isolated functions from host applications, but also vice versa, to access host application functions from isolated functions. The list of external functions allowed for calling from isolated functions is strictly managed. By default, access from isolated functions is limited to the minimum API that allows messages to be passed to the host application.
In the future, Microsoft plans to hand over this project to the non-profit Cloud Native Computing Foundation (CNCF) for joint development on a neutral platform independent of individual manufacturers. The CNCF operates under the wing of the Linux Foundation and oversees the development of projects such as Kubernetes, etcd, Cilium, Containerd, cri-o, Flux, Helm, Istio, and gRPC.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options: