Microsoft has activated a new account lockout policy in Windows 11 to protect users against password bruteforce attack. The change is already live in Insider builds of version 22H2. The policy will block the user account for 10 minutes if someone is trying to guess the password via RDP and other methods.
The new defaults look as follows.
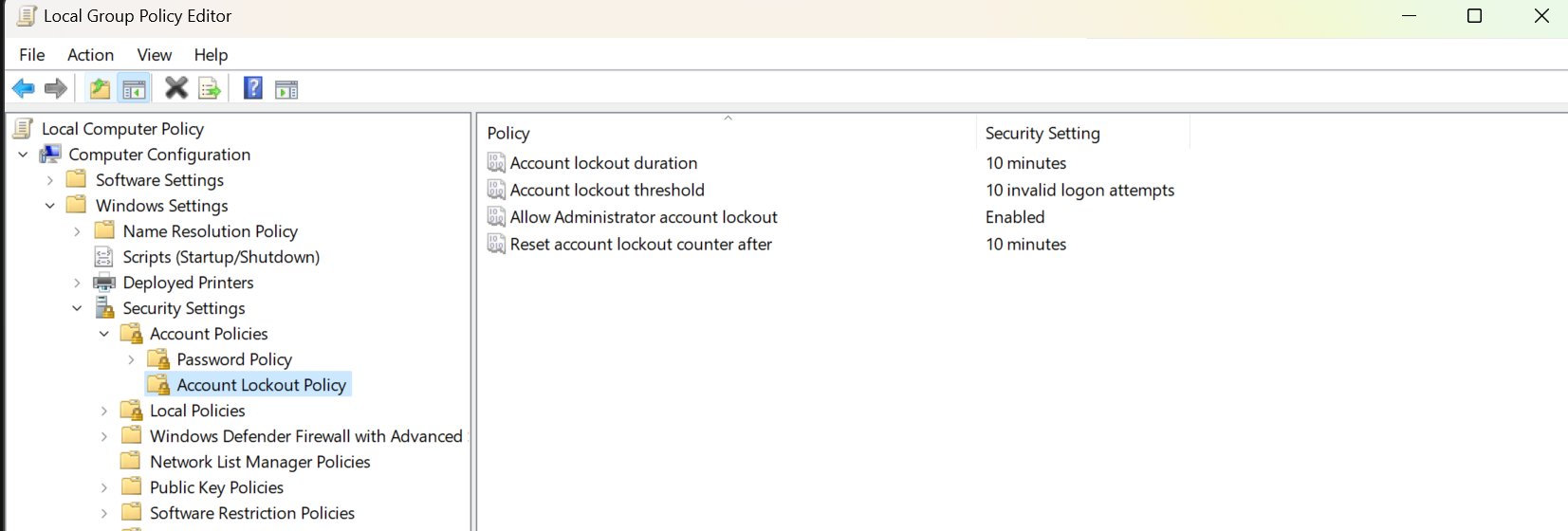
Windows 11 default account lockout policy
- The account will be locked for 10 minutes
- It will happen after 10 failed login attempts
- The lockout counter will be reset after 10 minutes
- Windows will protect all user accounts, including the built-in Administrator account.
You can change these values by opening the Local Group Policy editor (Win + R > gpedit.msc) and going to the Computer Configuration > Windows Settings > Security Settings > Account Lockout Policy category.
With the new defaults, it will be harder for an attacker get into the running system remotely and locally, even with a special software that guesses passwords automatically. Windows will limit the number of tries and will slow down the bad actor.
The new defaults are effective starting in Windows 11 version 22H2, which includes a bunch of other changes and improvements. However, these policy options exist in many previously released Windows versions, including Windows 10 and Windows 8. There you can enable and adjust them manually to secure you user account. Finally, Microsoft is about to port these new defaults to actual versions of Windows 10 and its Server counterparts.
via @dwizzzleMSFT
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won't take a lot from you, but it will help us grow. Thanks for your support!
Advertisеment

Now i am using Linux
Nice change from them. However over the years I’ve been targeted by attackers who control a lot of outgoing addresses and thus can workaround this protection using a different address every time. (So fortunate that my password entropy should be high enough to withstand such brute force attacks for like a billion years.) I feel that extra security measures are still much needed, like tunneling RDP through SSH authenticated only by a key pair.