It is not a secret to anyone who uses Windows 10 that this operating system is collecting a lot of private information and sending it back to Microsoft so they get more telemetry data. Many users are not happy that Windows 10 is spying on them and constantly seeking a way to stop it. While this is not the first time that we are referring to this issue, today I would like to share a different way to prevent Windows 10 from collecting your sensitive data using only the built-in Windows Firewall.
Advertisеment
In my previous article, How to disable Telemetry and Data Collection in Windows 10, I widely described what is telemetry and how Microsoft is collecting your data. Besides that, the article comes with a solution against collecting data without your approval.
Before we start, I definitely should mention one fact. Beware Windows 7/Windows 8 users, your operating system might be spying on you as well! See the following article: Telemetry and Data Collection are coming to Windows 7 and Windows 8 too
Now, let's see what we can do to prevent Windows 10 from spying on you using just Windows Firewall. The main idea behind this method is to block the well known list of Microsoft servers using the appropriate rules of Windows Firewall. This does not involve any third party tool in the process, which is also good. You will see and control what you are doing.
Let's see the following example:
netsh advfirewall firewall add rule name="telemetry_watson.telemetry.microsoft.com" dir=out action=block remoteip=65.55.252.43,65.52.108.29 enable=yes
The command above adds and activates a new rule which blocks outgoing connections to the server "telemetry_watson.telemetry.microsoft.com". Blocking will be performed using these IP addresses: 65.55.252.43,65.52.108.29.
This command should be executed in an elevated command prompt. This is not too hard. But when you need to block all telemetry servers, you can get tired running all the required command one by one. Just look at the complete list (a PowerShell snippet) below!
Set-NetFirewallProfile -all netsh advfirewall firewall add rule name="telemetry_vortex.data.microsoft.com" dir=out action=block remoteip=191.232.139.254 enable=yes netsh advfirewall firewall add rule name="telemetry_telecommand.telemetry.microsoft.com" dir=out action=block remoteip=65.55.252.92 enable=yes netsh advfirewall firewall add rule name="telemetry_oca.telemetry.microsoft.com" dir=out action=block remoteip=65.55.252.63 enable=yes netsh advfirewall firewall add rule name="telemetry_sqm.telemetry.microsoft.com" dir=out action=block remoteip=65.55.252.93 enable=yes netsh advfirewall firewall add rule name="telemetry_watson.telemetry.microsoft.com" dir=out action=block remoteip=65.55.252.43,65.52.108.29 enable=yes netsh advfirewall firewall add rule name="telemetry_redir.metaservices.microsoft.com" dir=out action=block remoteip=194.44.4.200,194.44.4.208 enable=yes netsh advfirewall firewall add rule name="telemetry_choice.microsoft.com" dir=out action=block remoteip=157.56.91.77 enable=yes netsh advfirewall firewall add rule name="telemetry_df.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.7 enable=yes netsh advfirewall firewall add rule name="telemetry_reports.wes.df.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.91 enable=yes netsh advfirewall firewall add rule name="telemetry_wes.df.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.93 enable=yes netsh advfirewall firewall add rule name="telemetry_services.wes.df.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.92 enable=yes netsh advfirewall firewall add rule name="telemetry_sqm.df.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.94 enable=yes netsh advfirewall firewall add rule name="telemetry_telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.9 enable=yes netsh advfirewall firewall add rule name="telemetry_watson.ppe.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.11 enable=yes netsh advfirewall firewall add rule name="telemetry_telemetry.appex.bing.net" dir=out action=block remoteip=168.63.108.233 enable=yes netsh advfirewall firewall add rule name="telemetry_telemetry.urs.microsoft.com" dir=out action=block remoteip=157.56.74.250 enable=yes netsh advfirewall firewall add rule name="telemetry_settings-sandbox.data.microsoft.com" dir=out action=block remoteip=111.221.29.177 enable=yes netsh advfirewall firewall add rule name="telemetry_vortex-sandbox.data.microsoft.com" dir=out action=block remoteip=64.4.54.32 enable=yes netsh advfirewall firewall add rule name="telemetry_survey.watson.microsoft.com" dir=out action=block remoteip=207.68.166.254 enable=yes netsh advfirewall firewall add rule name="telemetry_watson.live.com" dir=out action=block remoteip=207.46.223.94 enable=yes netsh advfirewall firewall add rule name="telemetry_watson.microsoft.com" dir=out action=block remoteip=65.55.252.71 enable=yes netsh advfirewall firewall add rule name="telemetry_statsfe2.ws.microsoft.com" dir=out action=block remoteip=64.4.54.22 enable=yes netsh advfirewall firewall add rule name="telemetry_corpext.msitadfs.glbdns2.microsoft.com" dir=out action=block remoteip=131.107.113.238 enable=yes netsh advfirewall firewall add rule name="telemetry_compatexchange.cloudapp.net" dir=out action=block remoteip=23.99.10.11 enable=yes netsh advfirewall firewall add rule name="telemetry_cs1.wpc.v0cdn.net" dir=out action=block remoteip=68.232.34.200 enable=yes netsh advfirewall firewall add rule name="telemetry_a-0001.a-msedge.net" dir=out action=block remoteip=204.79.197.200 enable=yes netsh advfirewall firewall add rule name="telemetry_statsfe2.update.microsoft.com.akadns.net" dir=out action=block remoteip=64.4.54.22 enable=yes netsh advfirewall firewall add rule name="telemetry_sls.update.microsoft.com.akadns.net" dir=out action=block remoteip=157.56.77.139 enable=yes netsh advfirewall firewall add rule name="telemetry_fe2.update.microsoft.com.akadns.net" dir=out action=block remoteip=134.170.58.121,134.170.58.123,134.170.53.29,66.119.144.190,134.170.58.189,134.170.58.118,134.170.53.30,134.170.51.190 enable=yes netsh advfirewall firewall add rule name="telemetry_diagnostics.support.microsoft.com" dir=out action=block remoteip=157.56.121.89 enable=yes netsh advfirewall firewall add rule name="telemetry_corp.sts.microsoft.com" dir=out action=block remoteip=131.107.113.238 enable=yes netsh advfirewall firewall add rule name="telemetry_statsfe1.ws.microsoft.com" dir=out action=block remoteip=134.170.115.60 enable=yes netsh advfirewall firewall add rule name="telemetry_pre.footprintpredict.com" dir=out action=block remoteip=204.79.197.200 enable=yes netsh advfirewall firewall add rule name="telemetry_i1.services.social.microsoft.com" dir=out action=block remoteip=104.82.22.249 enable=yes netsh advfirewall firewall add rule name="telemetry_feedback.windows.com" dir=out action=block remoteip=134.170.185.70 enable=yes netsh advfirewall firewall add rule name="telemetry_feedback.microsoft-hohm.com" dir=out action=block remoteip=64.4.6.100,65.55.39.10 enable=yes netsh advfirewall firewall add rule name="telemetry_feedback.search.microsoft.com" dir=out action=block remoteip=157.55.129.21 enable=yes netsh advfirewall firewall add rule name="telemetry_rad.msn.com" dir=out action=block remoteip=207.46.194.25 enable=yes netsh advfirewall firewall add rule name="telemetry_preview.msn.com" dir=out action=block remoteip=23.102.21.4 enable=yes netsh advfirewall firewall add rule name="telemetry_dart.l.doubleclick.net" dir=out action=block remoteip=173.194.113.220,173.194.113.219,216.58.209.166 enable=yes netsh advfirewall firewall add rule name="telemetry_ads.msn.com" dir=out action=block remoteip=157.56.91.82,157.56.23.91,104.82.14.146,207.123.56.252,185.13.160.61,8.254.209.254 enable=yes netsh advfirewall firewall add rule name="telemetry_a.ads1.msn.com" dir=out action=block remoteip=198.78.208.254,185.13.160.61 enable=yes netsh advfirewall firewall add rule name="telemetry_global.msads.net.c.footprint.net" dir=out action=block remoteip=185.13.160.61,8.254.209.254,207.123.56.252 enable=yes netsh advfirewall firewall add rule name="telemetry_az361816.vo.msecnd.net" dir=out action=block remoteip=68.232.34.200 enable=yes netsh advfirewall firewall add rule name="telemetry_oca.telemetry.microsoft.com.nsatc.net" dir=out action=block remoteip=65.55.252.63 enable=yes netsh advfirewall firewall add rule name="telemetry_reports.wes.df.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.91 enable=yes netsh advfirewall firewall add rule name="telemetry_df.telemetry.microsoft.com" dir=out action=block remoteip=65.52.100.7 enable=yes netsh advfirewall firewall add rule name="telemetry_cs1.wpc.v0cdn.net" dir=out action=block remoteip=68.232.34.200 enable=yes netsh advfirewall firewall add rule name="telemetry_vortex-sandbox.data.microsoft.com" dir=out action=block remoteip=64.4.54.32 enable=yes netsh advfirewall firewall add rule name="telemetry_pre.footprintpredict.com" dir=out action=block remoteip=204.79.197.200 enable=yes netsh advfirewall firewall add rule name="telemetry_i1.services.social.microsoft.com" dir=out action=block remoteip=104.82.22.249 enable=yes netsh advfirewall firewall add rule name="telemetry_ssw.live.com" dir=out action=block remoteip=207.46.101.29 enable=yes netsh advfirewall firewall add rule name="telemetry_statsfe1.ws.microsoft.com" dir=out action=block remoteip=134.170.115.60 enable=yes netsh advfirewall firewall add rule name="telemetry_msnbot-65-55-108-23.search.msn.com" dir=out action=block remoteip=65.55.108.23 enable=yes netsh advfirewall firewall add rule name="telemetry_a23-218-212-69.deploy.static.akamaitechnologies.com" dir=out action=block remoteip=23.218.212.69 enable=yes
So, to make this easy for you so you can add these rules quickly, I prepared a batch file for you. Run "add rules.cmd" and confirm the UAC prompt.
Download Block Telemetry Rules file for Windows 10
After that, you should see the following in Windows Firewall:
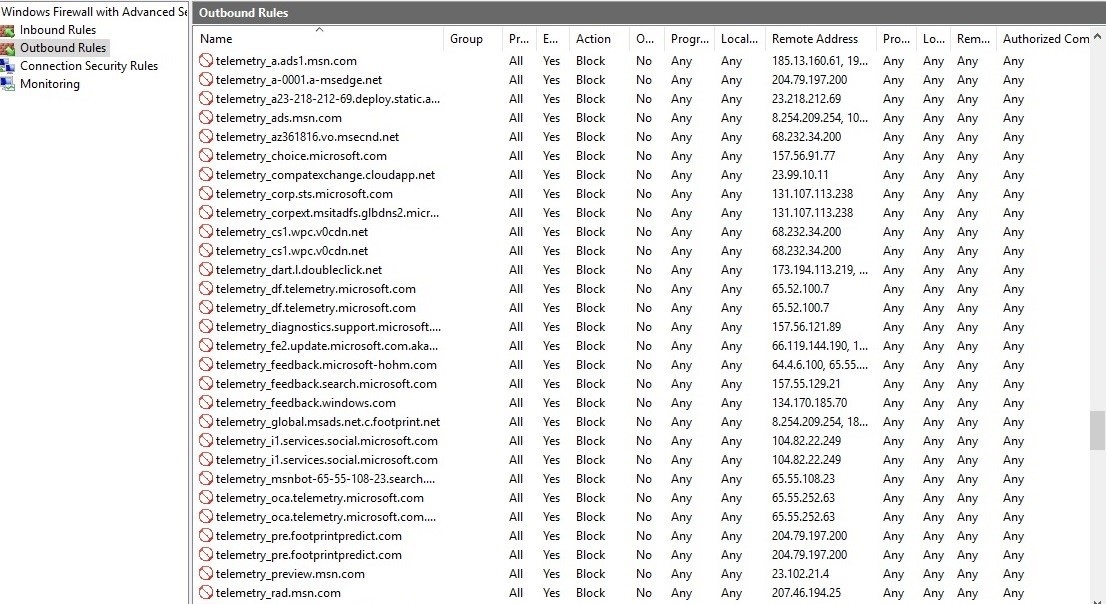
Windows 10 will not spy on you anymore. No third party tools were involved.
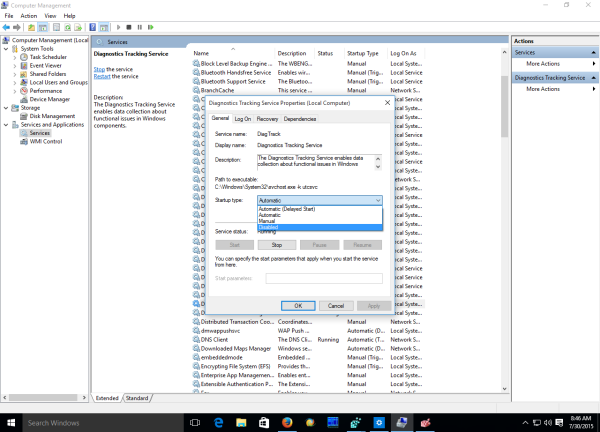
Now, go to Services and Applications -> Services in the left pane. In the Services list, disable the following services:
Diagnostics Tracking Service
dmwappushsvc
Double click the mentioned services and pick "Disabled" for the startup type:
 You need to restart Windows 10 for changes to take effect.
You need to restart Windows 10 for changes to take effect.
This last step will disable "keylogger", which might be sending data that you type. This step is not actually necessary, as all the servers are already blocked. However, when you update Windows 10, the server list might be changed by Microsoft and new servers might be added. So, by disabling the mentioned services, you can be sure that the OS will not collect and send the data secretly.
That's it. I am open to your questions. If you haven't understood something, let me know in the comments.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won't take a lot from you, but it will help us grow. Thanks for your support!
Advertisеment

A note on the Windows 7/8 telemetry update. If you already disabled the data collection option then those updates actually reduce the number of calls Windows makes to the Telemetry servers (not sure why it still makes any but whatever).
I follow the instructions given but i really don´t believe that Bill will be fooled by this rather “naive blocking thing”… Bill is to nasty to fall in this trap.
Of course, there is (hardware) encrypted data which is sent obfuscated through different protocols, diffused, so that it can’t be caught in billions of bytes, even if someone is looking for it. The “visible” stuff is there just to confuse and make things seem legit.
*This is the only way to run Windows 10, with everything disabled: i.imgur.com/R1tbqMS.png :)
Very radical way, isn’t it?
It’s a major pain. :( Half of the web does not load in the browsers, blah.
^^ Can’t edit, just to clarify – by saying “hardware encrypted” I mean that the Micro$oft operating system is working in tandem with companies like Intel and various (xEFI) BIOS manufacturers (& others!) in order to produce the capabilities to perform amazing backdoors (like Monty Python’s Flying Circus. :))
Things such as “Secure Boot” and many, many, other nowhere documented channels (perhaps some engineers might be able to recognize machine code, where such actions may be allowed; when looking at the CPU micro-architecture diagrams and whatnot, but even that is -very- doubtful).
It’s “deep undercover”, like Eddie Murphy in Beverly Hills Cop – and, also, just as ridiculous; except, much less entertaining, heh. xD
@https://www.youtube.com/watch?v=Oq3cGgqbWG8
If Windows were truly spying, this might be useful. But, since Windows is definitely not spying on us, I don’t find it useful at all.
Found the M$ employee.
haha
Then they won’t mind.
Cortana will be remember as the most evil character of all times. You my friend, poor fellow.. God bless you.
Hi Sergey,
I used the previous article for the two non-insider computers without a problem, and very much appreciate the ability to block data being transmitted to Microsoft. My question is this: Is one method preferable over the other? If it matters to your answer, I have Zemana anti-keylogger software installed.
For myself, I’d rather make a change to the Registry, with a backed-up Restore available, than mess around with a firewall and not be able to access anything or get online.
And as always, thanks for all your excellent work!
Regards,
Techie Bear
Well, in this method more servers will be blocked.
You can avoid the Registry editing.
Personally, I liked this method more than the previous one.
Problem is they can easily revert back to spying and make it more difficult to subvert with an update or just change their server IPs. Going to boycott windows altogether this year.
Yep yo are right. I also avoid Windows 10 on my PCs :)
Where do you think firewall rules are stored…. Yes, in the registry :)
DWS_lite does all this and more, is free, and constantly updated.
After adding firewall rules, Windows Update reports ‘We couldn’t get online to download your updates.’ If I remove the rules, Update works again.
Who is afraid of Windows update? That´s paranoia. I´ve working on W7 from the beginning without a single update. Not a single damn issue. The big problem with all Windows versions is just Windows updates!
I agree. I turned off updates and and don’t have viruses and it runs fine.
The updates are just a door for microsoft to get in your system, there may be some updates for security but I beleive most all of them are BS.
Using TCPView, tracked the problem to 134.170.51.190. Removed that IP from rules.ps1 and Update works again.
Lot of other IP in this list are mandatory to receive Upgrades, other service and diagnostic from Microsoft.
Some Paranoid grabbed all MSFT domain on the net and put it in a list.
One of those day you will lose lot of time to find why some Microsoft services don’t work ;-)
Quite possible.
Other than updates that I reserve the right to control MS can suck it. Any services I would take from them should be voluntary and not crammed down my throat.
Don’t use microsoft services.
sorry my English is translated with Google, I performed the entire procedure, everything went well, I can not enter the site Microsoft Answer Italian, can ‘be a firewall port blocked?
Quite possible.
Please tell me the url/link which you are trying to access?
the site is this
http://answers.microsoft.com/it-it?auth=1
not me access to my account and I favedere posts in all sections,
other Microsoft sites are fine, If these firewall rules we found that the site does not spy visit
thanks and sorry for my english
Let’s see it its IP address is in the blocking list.
I understand, I leave it,
the important thing is that the other Microsoft sites work well,
thank you
blocking this ip 68.232.34.200 breaks web.skype.com
isn’t adding domains into hosts file a better solution?
Try to spy the traffic.
Windows 10 can BYPASS the hosts file for telemetry!
WireShark can prove it.
wow, Microsoft is going in hard. Thx for your service man. I guess i’ll have to manage ip blocking on the case by case basis, e.g. when i’ll need access to some features i’ll disable the rules but will leave them enabled by default
They are corporatists after all. Into Biotech death panels, elitism and will do the NSA work, just as Google and all other tech companies are happy to oblige. If not then they’d not be in business, but then they don’t even try to protect our privacy. We have nothing to hide, privacy is our natural born right and our choice. It is time we be more assertive over the control others have over OUR life’s.
Can MS bypass windows firewall?
I always thought the firewall was independent of other processes. I am using windows 7 / Win 2008 64 bit. But I suppose in later versions of windows or with a patch, MS could just hack their own firewall. Do you recommend a 3rd party firewall or using an additional firewall on top of the windows firewall? If so, which one?
I am big fan of Zone Alarm.
Few years ago it was really great app.
an additional firewall on top of the ‘windows firewall’ – Zone Alarm will work.
most other firewalls will disable ‘windows firewall’.
Zone Alarm Free Firewall is not what it used to be, some features have been removed, a bit more buggy.
Blocking this IP also breaks access to Technet.
Tip: how to disable “development mode” http://answers.microsoft.com/en-us/windows/forum/windows_10-files/bug-windows-10-file-explorer-reopens-after-getting/596553df-3af6-4a96-ab52-0fedba4df1bd
WIndows Update won’t work if the firewall is set to block outgoing connection telemetry_fe2.update.microsoft.com.akadns.net.
If you simply remove that one firewall block that’s in your script, Windows Update will work again.
After appling this trick, I cannot access to bing.com or bing.maps
I finally found I need to remove the block of:
– telemetry_a-0001.a-msedge.net
– telemetry_pre.footprintpredict.com
– telemetry_pre.footprintpredict.com (it is repeated in Windows Firewall)
(with the help of Control panel -> trobleshooting -> connect to Internet -> help me to connect to a specific page)
Sorry for my english, I hope you understand me
Please remove “telemetry_fe2.update.microsoft.com.akadns.net” and the other ones from nabucco.
This is not very helpful if it blocks nearly everything. The list has to be updated.
PS.: Something blocks the locations search in the weather app.
Disable “Explorer.EXE_BLOCK” and “204.79.197.200_Block” IP for weather to work properly
You don’t need to remove them altogether, juste change the value “enabled=yes” to “enabled=no” at the end of each line in the file, with powershell.
Doing this to your firewall also blocks windows updates from accessing the web to update – DOH!
No, it doesn’t on Win 10.
That’s good. I can actually look at Windows updates before microsoft forces them down my computer.
Outbound block on IP 68.232.34.200, intended for:
cs1.wpc.v0cdn.net
az361816.vo.msecnd.net
blocks get: http://ajax.aspnetcdn.com/ajax/jQuery/jquery-1.11.1.min.js from answers.microsoft.com
http://answers.microsoft.com/en-us/feedback/forum/fdbk_commsite-bug/answersmicrosoftcom-doesnt-work-on-firefox-if-free/55a938e8-a06c-47c6-b241-72bd1d55a5a6?tm=1447152774954
Is there a script to reverse this block? I think i used it to block windows but now my workplace requires me to setup airwatch and connect to their servers but i’m not able to connect. I’m wondering if something in this process is blocking connection to airwatch as well.
Remove all custom rules from Firewall.
Windows Firewall, Restore Defaults.
So – now Bing won’t work after running the batch file. For some searches Bing is better than Google, so whilst I don’t like data gathering by either, I’d like to know which specific item to unblock for Bing to work.
why use an OS that spies on you and you go out of your way to block everything it tries to send out?
Be honest to yourself, if you dont want to get spied on use an other OS, otherwise stop nagging about privacy.
This is right, but there are people who are still hesitating going over to linux apparently. So these mitigating steps are a beginning, not a cure.
Bing = microsoft. They track your urls. Spy bot search and Destroy identify ms tracks and isolates them and gets rid of them. Nice$soft is developing the Linux system.
A lot of small businesses are forced to use Internet Explorer and other Windows features (usually caused by programmers only programming business apps for Windows that are not compatible with Linux, Firefox, or any other open source). Some government websites still only work with Internet Explorer, and the small businesses are required by law to access the websites, so the businesses have to use Windows or else go out of business. Home users usually have a choice, but all of my business customers are locked into Windows regardless of how much they hate Microsoft. On my personal PCs I use Windows for work, and Linux for fun. Someday when I quit my business and retire, I hope to only use Linux.
I have windows 10 64-bit OS (Fresh Installation). Amount these services I found 2 one but didn’t found first one in services…….?
1) Diagnostics Tracking Service
2) dmwappushsvc
I think Microsoft renamed it to “Connected User Experiences and Telemetry service”. Is information correct…..?
yep, you are right.
No such service in 10 Pro 64-bit version 1903.
I don’t use windows firewall,can I just add *.microsoft.com *.live.com,etc. to third party firewall?
Sure you can
Also have another question. Is there a way to delete/disable/freeze, etc certain processes, at the local computer level? I think this would be a more robust approach than only blocking firewall. Especially if updates are needed from time to time, I can
But I need a master list of all the Win 10 ‘spy’ exe’s, what they do, and how to block (disable) them. Of course microsoft is not going to tell us this, so it is up to the White Hat hackers and tech folks to compile this list.
Hello:
Thank you so much for providing info on how to restrain this data mining and tracking virus called Windows 10. There is one thing I would still like to get from microsoft, the latest windows defender virus definitions. If I follow these instructions, can someone kindly tell me what to unblock to permit defender to talk to the mothership, but nothing else?
“Diagnostics Tracking Service” is no longer in the list of services.
There is
Diagnostic Policy Service
Diagnostic Service Host
Diagnostic System Host
Which one should be disabled?
Thanks
You need to disable “Connected User Experiences and Telemetry”
disable this one: Connected User Experiences and Telemetry
ok and now the same please for linux/freebsd firewalls.. i think using a linux router and firewall may work even better as it may happen that m$ adds a bypass in windows for this.
Ever since i got a new dial up, my windows 10 was downloading stuff from akamai and others at like 10Mbps and it was really annoying. your post really helped me. although your program was for outbound blocking and my problem was more inboung, so a little tweak and the problem was solved
thanks a lot though.
Ran the batch file and confirmed the prompt – but rules do not appear in the firewall outbound rules section ????
Microsoft explains what windows telemetry collects and how to LIMIT but not stop what Microsoft actually collects and sends back. Windows Defender is even a involved. I would suspect that the services run can bypass the Windows firewall. Microsoft is determined to collect this information.
https://technet.microsoft.com/en-us/itpro/windows/manage/configure-windows-telemetry-in-your-organization
I follow the instructions given but i really don´t believe that Bill will be fooled by this rather “naive blocking thing”… Bill is to nasty to fall in this trap.
Do you mean Satya?
I created a simple BASH script to add these to a Linux firewall (iptables). I’ve commented the concerns mentioned in the posts above.
With the Windows Update group NOT blocked, I am able to run Windows Update on Windows 10 and Server 2012.
I have not checked Bing or Weather or Skype, I don’t care about those. I also don’t care about Cortana, so I’m not testing that.
https://dl.dropboxusercontent.com/u/59306089/telemetry.txt
Thank you for the cool table of telemetry servers! I felt like playing so I parsed your cool list into a powershell script that you can easily adapt and extend.
https://paste.ubuntu.com/21128315/
In case the pastebin is being deleted, here the script I used to setup the rules on my computer:
@(
@{ RemoteAddress=’191.232.139.254′; Name=’telemetry_vortex.data.microsoft.com’ }
@{ RemoteAddress=’65.55.252.92′; Name=’telemetry_telecommand.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.55.252.63′; Name=’telemetry_oca.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.55.252.93′; Name=’telemetry_sqm.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.55.252.43′; Name=’telemetry_watson.telemetry.microsoft.com’ }
@{ RemoteAddress=’194.44.4.200′; Name=’telemetry_redir.metaservices.microsoft.com’ }
@{ RemoteAddress=’157.56.91.77′; Name=’telemetry_choice.microsoft.com’ }
@{ RemoteAddress=’65.52.100.7′; Name=’telemetry_df.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.52.100.91′; Name=’telemetry_reports.wes.df.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.52.100.93′; Name=’telemetry_wes.df.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.52.100.92′; Name=’telemetry_services.wes.df.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.52.100.94′; Name=’telemetry_sqm.df.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.52.100.9′; Name=’telemetry_telemetry.microsoft.com’ }
@{ RemoteAddress=’65.52.100.11′; Name=’telemetry_watson.ppe.telemetry.microsoft.com’ }
@{ RemoteAddress=’168.63.108.233′; Name=’telemetry_telemetry.appex.bing.net’ }
@{ RemoteAddress=’157.56.74.250′; Name=’telemetry_telemetry.urs.microsoft.com’ }
@{ RemoteAddress=’111.221.29.177′; Name=’telemetry_settings-sandbox.data.microsoft.com’ }
@{ RemoteAddress=’64.4.54.32′; Name=’telemetry_vortex-sandbox.data.microsoft.com’ }
@{ RemoteAddress=’207.68.166.254′; Name=’telemetry_survey.watson.microsoft.com’ }
@{ RemoteAddress=’207.46.223.94′; Name=’telemetry_watson.live.com’ }
@{ RemoteAddress=’65.55.252.71′; Name=’telemetry_watson.microsoft.com’ }
@{ RemoteAddress=’64.4.54.22′; Name=’telemetry_statsfe2.ws.microsoft.com’ }
@{ RemoteAddress=’131.107.113.238′; Name=’telemetry_corpext.msitadfs.glbdns2.microsoft.com’ }
@{ RemoteAddress=’23.99.10.11′; Name=’telemetry_compatexchange.cloudapp.net’ }
@{ RemoteAddress=’68.232.34.200′; Name=’telemetry_cs1.wpc.v0cdn.net’ }
@{ RemoteAddress=’204.79.197.200′; Name=’telemetry_a-0001.a-msedge.net’ }
@{ RemoteAddress=’64.4.54.22′; Name=’telemetry_statsfe2.update.microsoft.com.akadns.net’ }
@{ RemoteAddress=’157.56.77.139′; Name=’telemetry_sls.update.microsoft.com.akadns.net’ }
@{ RemoteAddress=’134.170.58.121′; Name=’telemetry_fe2.update.microsoft.com.akadns.net’ }
@{ RemoteAddress=’157.56.121.89′; Name=’telemetry_diagnostics.support.microsoft.com’ }
@{ RemoteAddress=’131.107.113.238′; Name=’telemetry_corp.sts.microsoft.com’ }
@{ RemoteAddress=’134.170.115.60′; Name=’telemetry_statsfe1.ws.microsoft.com’ }
@{ RemoteAddress=’204.79.197.200′; Name=’telemetry_pre.footprintpredict.com’ }
@{ RemoteAddress=’104.82.22.249′; Name=’telemetry_i1.services.social.microsoft.com’ }
@{ RemoteAddress=’134.170.185.70′; Name=’telemetry_feedback.windows.com’ }
@{ RemoteAddress=’64.4.6.100′; Name=’telemetry_feedback.microsoft-hohm.com’ }
@{ RemoteAddress=’157.55.129.21′; Name=’telemetry_feedback.search.microsoft.com’ }
@{ RemoteAddress=’207.46.194.25′; Name=’telemetry_rad.msn.com’ }
@{ RemoteAddress=’23.102.21.4′; Name=’telemetry_preview.msn.com’ }
@{ RemoteAddress=’173.194.113.220′; Name=’telemetry_dart.l.doubleclick.net’ }
@{ RemoteAddress=’157.56.91.82′; Name=’telemetry_ads.msn.com’ }
@{ RemoteAddress=’198.78.208.254′; Name=’telemetry_a.ads1.msn.com’ }
@{ RemoteAddress=’185.13.160.61′; Name=’telemetry_global.msads.net.c.footprint.net’ }
@{ RemoteAddress=’68.232.34.200′; Name=’telemetry_az361816.vo.msecnd.net’ }
@{ RemoteAddress=’65.55.252.63′; Name=’telemetry_oca.telemetry.microsoft.com.nsatc.net’ }
@{ RemoteAddress=’65.52.100.91′; Name=’telemetry_reports.wes.df.telemetry.microsoft.com’ }
@{ RemoteAddress=’65.52.100.7′; Name=’telemetry_df.telemetry.microsoft.com’ }
@{ RemoteAddress=’68.232.34.200′; Name=’telemetry_cs1.wpc.v0cdn.net’ }
@{ RemoteAddress=’64.4.54.32′; Name=’telemetry_vortex-sandbox.data.microsoft.com’ }
@{ RemoteAddress=’204.79.197.200′; Name=’telemetry_pre.footprintpredict.com’ }
@{ RemoteAddress=’104.82.22.249′; Name=’telemetry_i1.services.social.microsoft.com’ }
@{ RemoteAddress=’207.46.101.29′; Name=’telemetry_ssw.live.com’ }
@{ RemoteAddress=’134.170.115.60′; Name=’telemetry_statsfe1.ws.microsoft.com’ }
@{ RemoteAddress=’65.55.108.23′; Name=’telemetry_msnbot-65-55-108-23.search.msn.com’ }
@{ RemoteAddress=’23.218.212.69′; Name=’telemetry_a23-218-212-69.deploy.static.akamaitechnologies.com’ }
) | ForEach-Object {
New-NetFirewallRule @_ -DisplayName $_.Name -Direction Outbound -Enabled True -Action Block
}
Thank you Michael.
Dang it, I missed the fact that some netsh commands are using multiple IPs in their remoteip arguments. I made some modifications:
https://paste.ubuntu.com/21140900/
It probably doesn’t make anything easier without a proper script-file but maybe it’ll help somebody. Haven’t been programming for half a year now and had to hack something up to quench my thirst :P.
The script add ruels.cmd works fine.
Is it usefull adding rules in microsoft firewall if kapersky internet security 2016 is installed on the computer ?
As much as I was hoping this would work, it does not. I’ve been on a mission to block microsoft from communicating from my personal network. I’m currently using a Palo Alto PA-4050 firewall for the network which allows me to see the logs. I’ve identified the IP ranges below as Microsoft owned IP addresses. I’m working from the standpoint that since microsoft rotates it’s IP addresses and not all of the metrics gathering have an FQDN I decided to block all of the Microsoft owned IP addresses. I applied both the rules above as well as the IP subnets I’ve identified so far as firewall rules and monitored from my firewall, I can still see the computer attempt to communicate with microsoft after these rules were applied. I wish I had a better solution but all I know is this solution doesn’t work.
Here’s the IP subnets I’ve identified as owned by MS so far. I don’t claim this to be a complete list, but identified from the traffic I’ve monitored and cross referenced with this site: http://www.tcpiputils.com/browse/ip-address
13.64.0.0/11
13.96.0.0/13
13.104.0.0/14
23.96.0.0/13
64.4.0.0/18
65.52.0.0/14
66.119.144/20
94.245.64.0/18
104.40.0.0/13
104.146.0.0/15
104.208.0.0/13
131.107.0.0/16
131.253.1.0/24
131.253.3.0/24
131.253.5.0/24
131.253.6.0/24
131.253.8.0/24
131.253.12.0/22
131.253.16.0/23
131.253.18.0/24
131.253.21.0/24
131.253.22.0/23
131.253.24.0/21
131.253.32.0/20
131.253.61.0/24
131.253.62.0/23
131.253.64.0/18
131.253.128.0/17
134.170.0.0/16
157.54.0.0/15
157.56.0.0/16
204.79.195.0/24
204.79.196.0/23
I have the Win 10 Anniversary update and had added rules to the firewall before the update. I ran the telemetry script found here and then went to take a look at the firewall today and noticed that ALL windows apps had explicitly set ALLOW for themselves. I had to go through each one changing ALLOW to BLOCKED. Tested with Microsoft Edge and when I open the app it complains about no internet connection, like I want it to.
Same thing for inbound rules now, they have gone through and set every one of their apps to explicitly have INBOUND set to ACCEPT. I hope none of their apps have some kind of remote execution vulnerability. I might have to go through and set my router to disable these so Microsoft can’t keep writing exceptions for themselves like the Clintons.
There are only 19,593,984 ip addresses owned by Microsoft (as of 9/2013, per ipinfo.io), to route the data through. Even the ip addresses for the monthly updates change regularly. Blocking ip addresses is a waste of time!!
Microsoft currently as the following AS numbers: 3598,8072,8068,26222,8069,13811,20046,6182,8075,23468.
I am a novice in regardds programming and this kind of work sdo it is a little hard for me to follow. If I understand not omly the original post, but the many responses my conclusion is that blocking ports is not any guarantee of stopping this telemetry. I may try it anyway in the abscense of another solution. But. would like to ask is DWS lite any good?
It claims to block the telemetry. Can you more experienced folks comment on this for me please?
Thank you all for your comments. I would add that it seems rather odd to me that anyone would suggest let alone adamently state that MS is not spying when they are using a key logger? how can this be n any way justified?
Great solution, I wish there was a way to test it. I did and image before I applied this just in case. Thanks Sergey
I have zero problems with Windows Update, all of you people that are doubting this and/or think a 3rd party app is better then use it, there is no need to post negative BS about this process, use the like or dislike button and grow up.
If Macroshaft have decided to spy on their users and have made Windows 10 a lean mean spying wouldn’t you think they would have built in loopholes into the native Firewall to prevent exactly what you are proposing? Your best bet is going with a 3rd party Firewall and even then it’s not 100% foolproof. This is not some Russian hacker trying to run a bitcoin client off your PC injected through some shady freeware, these are the guys who wrote the entire operating system the PC is running on. God know how many backdoors they’ve left for themselves.
You want a real solution? Reverse Engineer Direct X 12 and port an open source variant to Windows 7/8, MacOSX and Linux. Option 2, improve Vulkan to the point that it offers the same features as DX12. Make an open source version of Cortana that runs through some hive mind setup the way torrents do. Run it anonymously through Torr and DuckDuckGo. DX12 and Cortana are the king and queen of the MS chess pieces, you take them out of 10 and 10 will become irrelevant.
I’m not real good with computers but I typed in “add rules.cmd ” & a message pooped up stating Can’t find add check your spelling ?( I have a new desk top windows 10 computer.)
I found out that the ip address of a-0001.a-msedge.net changes every few minutes from 204.79.197.200 to 13.107.21.200. The latter ip address is not on the list meaning that the server is reachable when it has this ip address exactly then when something shall be transferred to it.
I found this incidently but this could of course be so with any other server as well.
Another option:
I have a router that can act as a DNS-server and there is also an option to set a DNS filter so that any DNS queries to the servers on the filter list won’t be resolved. If I activate this option and set the router as the only DNS server in all client computers (manual or using DHCP), this should solve the problem with changing ip addresses, right?
you can use the MS domain names and others and stick them in your custom hosts file and redirect back to yourself, should have same effect and block those domains, for the guy who said the firewall block did not work regardless of the rules then maybe the hosts file edit will work unless they use some service to sneak past somehow. Maybe a router firewall is more secure… i think UNIX is the way forward and just do a dual boot and keep windows only for what you really need it for
What about the service called “Microsoft (R) Diagnostics Hub Standard Collector Service”?
Thank you Winaero for this excellent script! :)
Also, I want people to know I found a similar script which blocks a bigger list of servers:
httр://sеrvilоn.соm/hоw-tо-disаblе-tеlеmеtry-оn-windоws-10/
I’ve run both scripts on my machine for maximum protection! :)
You should use WindowsSpyBlocker (https://github.com/crazy-max/WindowsSpyBlocker).
Rules (hosts / ips) are frequently updated!
For some reason after disabling telemetry my file explorer keeps rebooting at regular instances like evry 45 minutes pls do help out
Are you sure the issue is connected with firewall rules?
If so, try to disable rules one by one and see which causes the issue.
Rules (hosts / firewall) are frequently updated on WindowsSpyBlocker (https://github.com/crazy-max/WindowsSpyBlocker), you should talk about it Sergey !
Would applying these ip address’s to the host file have any effect?
I’ve heard the OS can ‘ignore’ the hosts file.
Windows 10 Fall Creators Update still spying on me even though I did stopped Windows 10 Fall Creators Update with Firewall
I never know if there is any way like this. a very clear way. But what if it happens again? whether to do the same thing?
some of the domains are hardcoded into the dns file, so it bypasses hosts file along with the firewall I think
Duplicate entries:
netsh advfirewall firewall add rule name=”telemetry_cs1.wpc.v0cdn.net” dir=out action=block remoteip=68.232.34.200 enable=yes
netsh advfirewall firewall add rule name=”telemetry_df.telemetry.microsoft.com” dir=out action=block remoteip=65.52.100.7 enable=yes
netsh advfirewall firewall add rule name=”telemetry_i1.services.social.microsoft.com” dir=out action=block remoteip=104.82.22.249 enable=yes
netsh advfirewall firewall add rule name=”telemetry_pre.footprintpredict.com” dir=out action=block remoteip=204.79.197.200 enable=yes
netsh advfirewall firewall add rule name=”telemetry_reports.wes.df.telemetry.microsoft.com” dir=out action=block remoteip=65.52.100.91 enable=yes
netsh advfirewall firewall add rule name=”telemetry_statsfe1.ws.microsoft.com” dir=out action=block remoteip=134.170.115.60 enable=yes
netsh advfirewall firewall add rule name=”telemetry_vortex-sandbox.data.microsoft.com” dir=out action=block remoteip=64.4.54.32 enable=yes